- Career steps
- Career overview
- Important skills
- What do security consultants do?
- Job description
- Salary and outlook
The top recommendations for “how to become a security consultant” can be broken down into four steps:
- Education: Obtain a bachelor’s degree in a related field like computer science, information technology, or cybersecurity. Based on Cyberseek‘s data, 3 percent of security consultants earned an associate degree, 37 percent of them obtained a bachelor’s degree, and 60 percent pursued a master’s.
- Gain Experience: Start with roles like network administrator, system analyst, or security analyst to gain practical experience in IT and security.
- Certifications: Earn industry-recognized certifications such as Certified Information Systems Security Professional (CISSP), Certified Information Security Manager (CISM), Certified Information System Auditor (CISA), Certified Ethical Hacker, and CompTIA Security+.
- Develop Soft Skills: Enhance your communication, critical thinking, and project management skills.
Ad
cybersecurityguide.org is an advertising-supported site. Clicking in this box will show you programs related to your search from schools that compensate us. This compensation does not influence our school rankings, resource guides, or other information published on this site.
Featured Cybersecurity Training
| School Name | Program | More Info |
|---|---|---|
| UC Berkeley School of Information | Online Master’s in Cybersecurity | No GRE/GMAT Required | website |
| Southern New Hampshire University | Online BS in Cybersecurity or Online MS in Cybersecurity | website |
There are many roles that a security consultant may specialize in, as the list below from George Washington University shows. Most security consultants will cycle through some of these roles throughout their careers. It is not unusual for a security consultant to fill a few roles simultaneously (including many of the roles listed on the career hub).
Preparing for a career as a security consultant
- Networking basics – Security consultants protect data and devices on a network. You need a good understanding of networking to be effective in security.
- Cybersecurity basics – You may be excited about learning how networks are breached, but take the time to understand the basics. Check out TechRadar’s article on free online training in cybersecurity.
- Learn coding and/or scripting – Python, Javascript, PowerShell, Node.js, Bash, Ruby, and Perl are all good to know.
- Build a lab – Book knowledge alone is not going to give you the skills you need. Hands-on experience is also really important. Some training should give interested people the knowledge needed to build a home lab. Don’t let the term “lab” scare you off. You can build a good lab with minimal resources at little expense. Get ideas at Infosec Reference.
- Get certified – This is a bit tricky. There are many cybersecurity certifications to choose from and you never know which a potential employer will value. There are free courses online for some certifications but the exams themselves are very expensive. Many companies will pay employees for additional training and certification. Being able to demonstrate cybersecurity knowledge and skills is much more important than getting a certification. Your skills will get the job, then pursue certification.
Here’s a list of certifications requested for security consultants:
What is a security consultant?
A security consultant is an information security professional who is trained to protect the confidentiality, integrity, and availability of data and network devices.
There are many ways to provide such protection. If Alice and Bob are cybersecurity consultants, Alice may be a security architect, designing security controls for many client companies, while Bob is a security administrator, configuring and maintaining security devices for his company.
Security consultants work as employees or as independent consultants. Entry-level consultants may start out configuring security devices. Those with years of experience in advanced roles may consult as a virtual chief information security officer (vCISO), helping organizations set and implement a security strategy.
Cybersecurity consultants are hackers — not malicious hackers, but hackers in the true sense of the word; people who are inquisitive and learn how to solve problems using technology. They are lifelong learners by nature, an essential trait for several reasons:
- The security landscape is constantly changing, as threats become more sophisticated. Attackers are constantly changing their methods.
- Technology changes at a rapid pace, so knowledge and defenses need to advance with it. One example is cloud computing, which requires a different approach to security than on-premise security.
- The increasing number of major breaches have organizations demanding more effective security solutions than ever before.
Security consultant skills and experience
A successful security consultant must have both technical skills and soft skills. It is tempting to focus on technical skills while underestimating the need for soft skills. Do not make that mistake!
This list includes technical and soft skills that are typically required for information security consultants. They are extracted from actual job listings on sites like Indeed and Glassdoor.
- Technical skills
- Adept at understanding the overall security/threat landscape and proposing solutions to mitigate risks from this environment
- Must have a good understanding of IT infrastructure architecture
- Security certifications such as CISA, CISM, CISSP, CEH, and Security+.
- Experience advising customers on architectures meeting industry standards such as PCI DSS, ISO 27001, HIPAA, GDPR
- Experience working with firewalls, load balancers, proxies, VPNs, endpoint security tools AV, IPS, SSL inspection, SIEM or security monitoring platforms
- Strong knowledge of OSI Layer 7 Model, Network Architecture, and Network Topology.
- Soft skills
- Experience as a project lead, and the ability to drive to completion and maintain schedules.
- Excellent documentation and organization skills
- Excellent oral, written, and presentation skills
- Must be an intelligent, articulate, and persuasive individual who can serve as an effective advisor to the senior client security leadership
- Should be able to communicate security-related concepts to a broad range of technical and non-technical staff and drive security across multiple teams
- Ability to travel to customer sites as needed
- Demonstrated ability to think strategically about business, product, and technical challenges
Top skills for security consultants:
- Cyber Security
- Computer Science
- Identity And Access Management
- Vulnerability
- Authentications
- Microsoft Azure
- Project Management
- Cloud Security
- Incident Response
Future skills projected for security consultants:
- Security foundation & threat intelligence
- Cloud Security
- Preventative antivirus
- Cloud access security broker (CASB) management
- Enterprise mission assurance support service
What do security consultants do?
Cybersecurity consultants fight the never-ending battle for truth, justice, and… Wait, that’s Superman. But hyperbole aside, security consultants do fight a never-ending battle against the bad guys — malicious hackers — in what is effectively an arms race.
At the most fundamental level, security consultants make the Internet and corporate networks safer places. They plan, design, build, configure, code, run, maintain, and/or monitor security controls meant to protect data and networks from being breached. Yes, that’s a mouthful, but it easily could have been longer.
Security consultants take actions to make it difficult for anyone to gain unauthorized access to data or network devices and to do harm. There is almost no limit to the number of ways to do so.
They fall into the general categories of prevention, detection, and response. Security consultants who handle prevention may plan, build, and configure security controls, while those who handle detection and response may code and monitor.
Remember Alice, the security architect? She handles prevention. Before she arrived, her company was the victim of a major data breach. The attacker accessed a system using an administrator account that used only a username and password that had been compromised. It became Alice’s responsibility to prevent that and other attacks in the future.
She assessed the existing security controls and designed a new set of controls she believed would be more effective. The first change she made was to require multi-factor authentication for all administrator accounts. In other words, more than just a password was required to access those accounts. That will prevent an attack similar to the one they had experienced.
Bob, the security administrator, worked on detection. He set up security monitoring to detect suspicious attempts to access systems. He also helped with prevention by configuring stricter access rules on the firewall. So, there are many roles for security consultants, and one person can have several roles.
Security consultant job description
We have established that security consultant roles can vary from one particular job to another. Here’s a list of common job titles related to security consultant:
- Security Consultants
- Delivery Consultants
- Program Officers
- IAM Developers
The mentioned job titles above will vary their job description as well. Yet some elements show up in many job descriptions. Let’s take a job description that was posted on Indeed by Amazon Web Services for a senior security consultant and break it down.
- 3+ years of experience with compliance and security standards
Compliance and standards are a big part of security. Security controls typically have to meet standards like PCI DSS, ISO 27001, HIPAA, or GDPR. Security consultants are expected to be familiar with these and other standards.
- Technical degree or equivalent experience
The breakdown: Some jobs require a degree but others do not. Either way, applicants should be able to demonstrate the knowledge and skills gained through experience.
- This position is for a highly technical, subject matter expert who can dive deep and work with customers to address the security, risk, and compliance needs of their AWS migrations.
The breakdown: Subject matter expert implies that you have a great depth of knowledge in a specific area. However, you still need a breadth of knowledge across multiple security topics, as well as general networking knowledge.
- You will have a passion for educating, training, designing, and building cloud solutions for a diverse and challenging set of intelligence community customers. You will enjoy keeping your existing technical skills honed and developing new ones, so you can make strong contributions to deep architecture discussions.
The breakdown: Technical skills and knowledge are not enough. Being part of a security team is a collaborative effort. Sharing your knowledge and learning from others is the best way to succeed.
- Consultants may be required to travel to client locations to deliver professional services as needed (50 to 75 percent).
The breakdown: Most consultant jobs require some travel. Decide how much travel is acceptable and be sure you understand what the expectations are for any given job.
- Deep understanding of Cloud Computing technologies and migration challenges. Professional experience architecting/deploying/operating solutions built on AWS.
The breakdown: AWS is a cloud computing environment, so an understanding of this area is to be expected. But with the rate at which organizations are adopting cloud computing, some knowledge in this area is expected for most cybersecurity jobs.
- Experience in technology/software sales consulting or equivalent skills.
The breakdown: Some security consultants support sales of their company’s security products and services.
This is just one example. A skill that is often required that is not in this particular description is coding or scripting. Common requirements include PowerShell, Python, Node.js, Javascript, Bash, Ruby, and Perl. Project management skills are also in demand.
Looking for more information about careers in cybersecurity?
Outlook for security consultants
Security consultants will play a vital role in developing innovative solutions to protect critical information and computer networks from increasingly frequent and sophisticated cyberattacks. This field is expected to grow 33 percent from 2023 to 2033, creating an average of 16,800 new job openings each year.
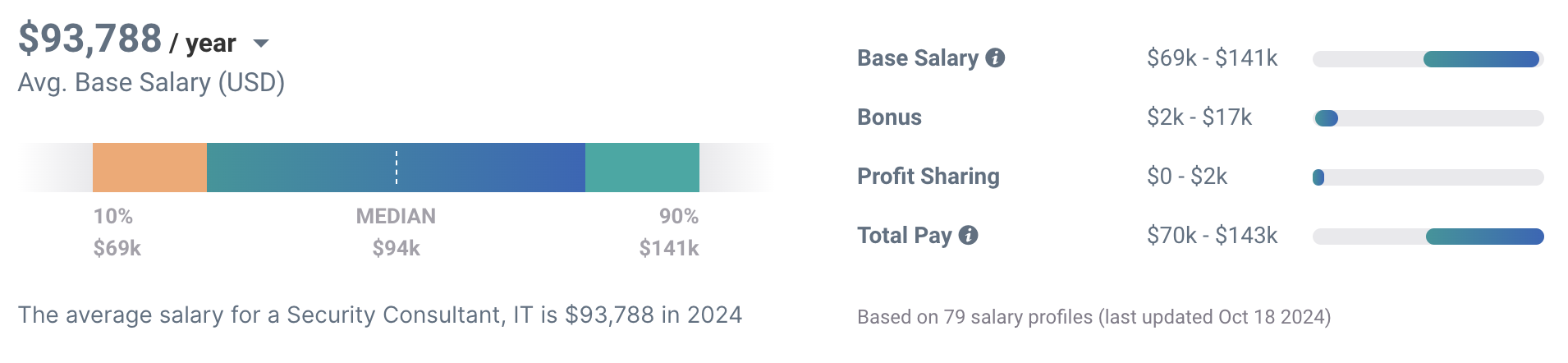
How much do security consultants make?
As of 2024, a security consultant’s salary range typically falls between $69,000 and $141,000 with an average of $93,788 per year. Salary ranges can vary widely based on educational background, certifications, additional skills, and the number of years you have spent in your profession as stated by Payscale.com.
Frequently asked questions
Security consultants are experts who advise organizations on security matters. They assess an organization’s security posture and recommend improvements. They cover a wide range of topics, including network, application, data, and physical security
Security consultants help organizations improve their security posture by evaluating their current security policies and procedures, identifying potential risks, and recommending solutions. They may also develop security policies and procedures, implement security controls, and monitor the organization’s security posture
To get started, develop a strong understanding of the security industry, its threats, and solutions. Build a network of contacts by attending industry events, joining professional organizations, and networking with other security professionals. This will help you stay up-to-date on the latest trends and technologies, as well as get certifications and build relationships with potential clients
Security consultants need a strong technical foundation and a deep understanding of computer networks, operating systems, and security protocols. They must also stay up-to-date on the latest security technologies, identify potential vulnerabilities, and conduct security audits
Typically, a bachelor’s degree in fields like computer science, information technology, or cybersecurity is necessary. Some roles may require a master’s degree in a specialized area of cybersecurity.
Experience in IT roles such as system analyst, network administrator, or security analyst can provide practical exposure to security concepts and best practices.
Relevant certifications include Certified Information Systems Security Professional (CISSP), Certified Information Security Manager (CISM), Certified Information System Auditor (CISA), Certified Ethical Hacker, and CompTIA Security+.
Usually, it begins with a degree in a related field, followed by gaining experience in IT or security roles, earning relevant certifications, specializing in a particular area of security, and continually updating skills and knowledge.
Sources
- Security Consultant career pathway | Sourced from cyberseek.org in Nov 2024.
- Salary information for Security Consultant | Sourced from Payscale.com in Nov 2024.