- Career steps
- Career overview
- Important skills
- What do digital forensics do?
- Job description
- Salary and outlook
Pursuing a digital forensics degree opens up a world of opportunities in our increasingly digital and cyber-centric society. This degree and career path is beneficial for several compelling reasons:
- Growing demand: The integration of technology into every facet of our lives has led to a surge in the need for digital forensics experts.
- High salary potential: The specialized nature of the work and market demand often equate to competitive compensation.
- Career variety: A degree in this field can lead to numerous roles, such as a digital forensic investigator or cybersecurity analyst.
- Constant learning: The ever-evolving nature of digital forensics promises continuous learning and professional growth.
- Impact: Digital forensics professionals play a vital role in safeguarding information systems, offering a sense of fulfillment.
- Skill transferability: The skills acquired during the study are highly transferable across various tech jobs.
- Job security: Given the relentless rise of cyber threats, job security is typically high in this field.
Ad
cybersecurityguide.org is an advertising-supported site. Clicking in this box will show you programs related to your search from schools that compensate us. This compensation does not influence our school rankings, resource guides, or other information published on this site.
Featured Cybersecurity Training
| School Name | Program | More Info |
|---|---|---|
| Southern New Hampshire University | Online BS in Cybersecurity or Online MS in Cybersecurity | website |
| UC Berkeley School of Information | Online Master’s in Cybersecurity | No GRE/GMAT Required | website |
The digital CSIs of the infosec universe, and digital forensics (sometimes known as DFOR) experts are critical in minimizing any harm done by cybercrimes, and reconstructing the crime to help bring criminals to justice.
Anytime law enforcement officials are involved, following the letter of the law is vital to a successful culmination of an investigation. Adhering to proper evidence-handling procedures will be of paramount concern for digital forensics experts.
Many digital forensic experts are employed by governments or government contractors. For a large portion of these positions, a security clearance is necessary.
Four steps to becoming a digital forensics expert
1. Education: There are a variety of college degree programs that lend themselves to careers in digital forensics. These include computer engineering, computer science, electrical engineering, applied mathematics, cybersecurity, information technology, and digital forensics. More advanced positions in digital forensics sometimes require master’s degrees.
Cyberseek data indicates that 2 percent of employed cyber crime analysts, a role similar to digital forensics, have obtained at least an associate degree. Meanwhile, 50 percent of this group have graduated with a bachelor’s degree, and about 48 percent have pursued a master’s degree.
2. Career path: There are entry-level positions available in digital forensics that provide excellent avenues of entry into the field. Honing technical skills as a prelude to developing infosec skills is also a viable path. So too are positions in information technology fields with a special focus on cybersecurity. Software development is another track that can lead to digital forensics careers.
3. Professional certifications: There are many different digital forensics certifications available, but some of the most popular and highly regarded include:
- GIAC Certified Forensic Analyst (GCFA): Covers the essential skills needed to conduct digital forensic investigations. It is a good choice for beginners and experienced professionals alike.
- GIAC Certified Forensic Examiner (GCFE): This more advanced certification is designed for experienced digital forensic investigators. It covers a wider range of topics, including incident response, malware analysis, and network forensics.
- EnCase™ Certified Examiner (EnCE): Certification for both private and public sector professionals in the use of EnCase forensic software
- AccessData Certified Examiner (ACE): Demonstrates proficiency with Forensic Toolkit (FTK) technology.
- Certified Forensic Computer Examiner (CFCE): Vendor-neutral certification that is designed for experienced digital forensic investigators.
- Certified Computer Examiner (CCE): Covers the process of digital forensics examination including the ability to handle and process digital evidence.
Other certifications include:
- Professional Certified Investigator (PCI)
- Computer Hacking Forensic Investigator (CHFI)
- GIAC Reverse Engineering Malware (GREM)
- GIAC Network Forensic Analyst (GNFA)
- GIAC Advanced Smartphone Forensics (GASF)
- GIAC Cyber Threat Intelligence (GCTI)
- Certified Mobile Device Examiner (CMDE)
- Certified Digital Forensics Examiner (CDFE)
- Certified Network Forensic Analysis Manager (CNFAM)
- Advanced Digital Forensic Certification (ADFC)
Some employers may also require more basic certifications, such as CompTIA A+ or Net+, which relate to IT operational and technical support skills or a more focused on one or a few specific types of hardware or operation systems like iOS Forensics, which delves into Apple’s notoriously challenging iPhone operating system.
4. Keep current: As with most cybersecurity career paths, it is vital to remain current with what is happening in the industry. Keeping skills and knowledge up to date with all of the latest trends is made easier when the field has its professional trade association. One example within the digital forensics community is the High Technology Crime Investigation Association.
Offering relevant continuing education, professional training, and proficiency testing for digital forensics professionals.
The Scientific Working Group on Digital Evidence (SWGDE) is another cybercrime forensics organization dedicated to keeping industry professionals’ knowledge and skills current. SWGDE focuses on fostering open communication between industry organizations and professionals.
What is a digital forensics expert?
Job titles for digital forensics professionals vary quite a bit but are generally variations on a theme. Titles seen frequently include digital forensics engineer, digital forensics investigator, digital forensics specialist, digital forensics analyst, digital forensics examiner, digital forensics technician, and others.
Job scope probably varies a little less than titles, but will depend on seniority and experience levels. Cybercrime forensics experts primarily enter the picture after there has been a breach of information security. That’s the time to put on the CSI trench coat and dig deep into the evidence. No blood and guts, just digital trails.
Digital forensics degree, skills, and experience
The investigations of digital crimes (and just about everything else) involve delving into computing devices, including mobile devices, software, network traffic analysis, memory analysis, media analysis, databases, and internet-of-things (IoT) devices. This means that digital forensic experts must possess in-depth and low-level knowledge of as many such systems as possible.
Technical Skills may include:
- Operating Systems Proficiency: An understanding of various operating systems such as Windows, MacOS, Linux, and their respective file systems.
- Forensic Tool Expertise: Familiarity with popular digital forensic tools such as EnCase, Forensic Toolkit (FTK), Autopsy, Cellebrite, X-Ways, and others.
- Mobile Forensics: Skills related to extracting and analyzing data from mobile devices like smartphones and tablets.
- Network Forensics: Knowledge of network protocols, packet analysis, and the ability to analyze network logs for signs of malicious activity.
- Cryptography: Understanding encryption and decryption techniques, recognizing encrypted files or data streams, and methods to potentially decrypt or analyze them.
- Malware Analysis: Ability to detect, isolate, and analyze malicious software.
- Cloud Forensics: Skills to investigate data stored on cloud platforms such as AWS, Google Cloud, or Microsoft Azure.
- Database Forensics: Ability to navigate and analyze database structures, logs, and data.
- Data Recovery: Techniques to retrieve data from damaged, encrypted, or formatted storage devices.
- Computer Languages: Python, Bash/Shell, and PowerShell are the most useful scripting languages for most digital forensics practitioners. If you are interested in specialized areas like malware analysis, then deeper knowledge in C/C++, Assembly, and Java may be more relevant
Soft skills sought by employers include Written and oral communication, excellent analytical skills, the ability to organize complex investigations, and the ability to document and report findings to stakeholders.
What do digital forensics experts do?
Today, there is a digital element to almost every legal investigation. From civil cases like infidelity, child custody, accident reconstruction, civil disputes, and missing persons, to criminal cases such as fraud, espionage, arson, larceny, and wrongful death, digital forensics is now used as a critical element of most investigations. Breach of information security is a major focus for digital forensics experts.
In the pursuit of finding answers, digital forensics professionals utilize skills and knowledge of all elements of information systems and security to extract all relevant data. This includes a wide variety of computer hardware and software, networking systems, and mobile devices and systems.
With this knowledge, digital forensics professionals will attempt to restore deleted data, analyze recovered data, and perform a complete forensic examination of all computers, databases, and systems.
This information is assembled and used to reconstruct what actually happened and then reported on to affected parties. In civil or criminal cases that have progressed to legal courts, digital forensics experts are often called on to provide expert testimony.
Digital forensics expert job description
The specific functions of digital forensics experts will vary substantially based on the employer’s agenda and the specific case being worked on. Potentially, tasks will include some or all of the following:
- Utilize leading forensic software to identify, collect, preserve, and analyze electronic data from laptops, desktops, servers, backup media, mobile devices, and a wide variety of other media
- Recover deleted user data, hidden data, file fragments, and temporary files
- Managing and tracking electronic evidence
- Identify and document tactics, techniques, and procedures used by an attacker to gain unauthorized access
- Develop and disseminate engagement reports, technical reports, and briefs based on analytic findings
- Follow industry-standard forensic best practices while imaging, preserving, transporting, and handling electronic data and associated physical devices.
- Provide expert witness testimony
Outlook for digital forensics
The Bureau of Labor Statistics projects that the employment of forensic science technicians, which includes digital forensics investigators, will grow 14 percent from 2023 to 2033.
Digital forensics investigators are in high demand in a variety of industries, including law enforcement, government, and private companies. As organizations become more reliant on digital technology, the need for digital forensics investigators to investigate cybercrimes and incidents will continue to grow.
In addition to the growing demand for digital forensics investigators, the field is also becoming increasingly complex as technology evolves. Digital forensics investigators need to be able to stay up-to-date on the latest trends and technologies to effectively investigate cybercrimes.
Law enforcement agencies, including district attorney offices, police, the FBI, DEA, and CIA, are often hiring digital forensics investigators. The FBI recently created the Forensic Examiner Talent Network to attract and retain top talent in cybercrime forensics.
How much do digital forensics experts make?
Glassdoor reports that in 2025, Digital forensics professionals make an average annual salary of $93k Bonuses, commissions, and profit-sharing can add as much as $20k annually. A quick search of job posting sites uncovered one position that paid $123k.
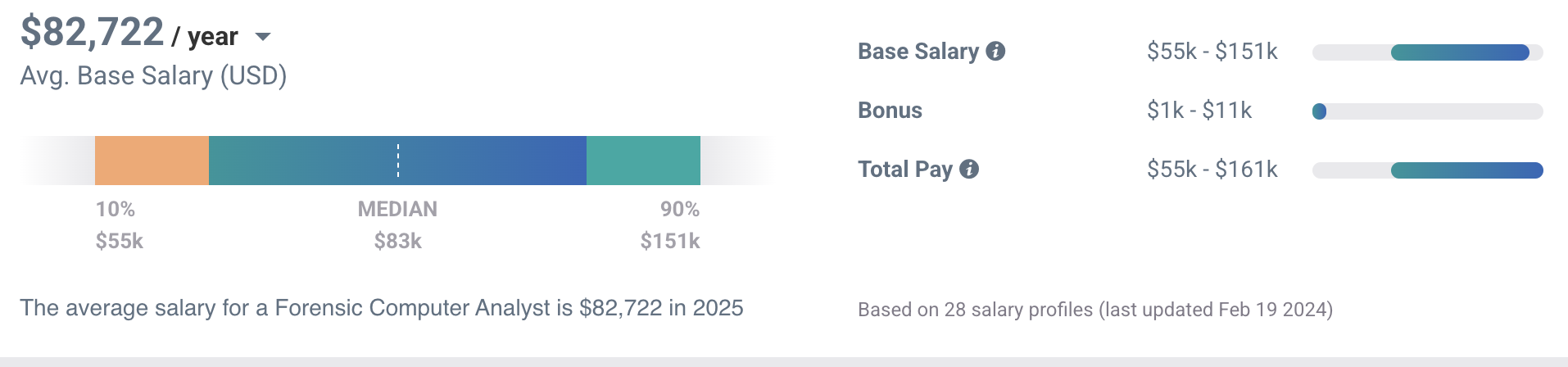
On the other hand, Payscale shared that the salary of a Forensic Computer Analyst with digital forensic skills may range from $55,000 up to $151,000, with an average salary of $82,722.
Frequently asked questions
Digital forensics experts identify, acquire, process, analyze, and report data. They usually come into play when a breach of information security has occurred.
A digital forensic expert helps retrieve, analyze, and complete a forensic examination of all computers, databases, and systems for affected parties.
Obtain a relevant degree (e.g., Computer Science or Digital Forensics) and consider certifications like CCE or GCFA. Develop technical and soft skills, emphasizing hands-on experience with forensics tools. Gain practical experience through internships and simulated labs and continuously update your knowledge in this rapidly evolving field. As you progress, consider specializing in areas like mobile forensics or malware analysis for advanced opportunities
Digital forensics is highly promising. As our reliance on digital platforms grows and the cyber threat landscape becomes more intricate, the expertise of digital forensic professionals will be indispensable in ensuring digital justice, security, and resilience.
Essential skills for digital forensic experts include proficiency in operating systems, file systems, digital forensic tools, encryption, malware analysis, cloud forensics, data examination, pattern recognition, legal procedures, and evidence admissibility. Recognized certifications, such as CCE, CFCE, or EnCE, are also valuable.
Sources
- Digital Forensics career pathway | Sourced from cyberseek.org in Feb 2025.
- Salary info for Digital Forensics | Sourced from Payscale and Glassdoor in Feb 2025.
- Outlook info for Digital Forensics | Sourced from Bureau of Labor Statistics in Feb 2025.