- Career steps
- Career overview
- Important skills
- What do security incident resp do?
- Job description
- Salary and outlook
Computer security incident responders can be found in large corporations and small businesses alike. They are needed in government entities and non-profits. They can be an integral part of an in-house security team or an independent consultant.
Ad
cybersecurityguide.org is an advertising-supported site. Clicking in this box will show you programs related to your search from schools that compensate us. This compensation does not influence our school rankings, resource guides, or other information published on this site.
Featured Cybersecurity Training
| School Name | Program | More Info |
|---|---|---|
| Purdue Global | Online BS in Cybersecurity | website |
| UC Berkeley School of Information | Online Master’s in Cybersecurity | No GRE/GMAT Required | website |
| Southern New Hampshire University | Online BS in Cybersecurity or Online MS in Cybersecurity | website |
Regardless of the organization, the incident responder, first and foremost, provides the first line of defense after an attack is suspected or has been detected.
Just as police and firefighters respond to immediate physical threats, the incident responder answers the call from computer defensive systems and wields the digital tools of a computer forensic analyst. They quickly respond to neutralize the immediate threat, bring order and control to the situation, and document the crisis for attribution and possible legal prosecution.
Like their physical security counterparts, incident responders often work irregular hours during a security incident and immediately after while providing investigative services. Individuals seeking a career in this specialty should expect to work for long and unpredictable periods, on occasion, that will be compensated by flex-time rules afterward.
Steps to becoming a computer security incident responder
As with most cybersecurity careers, there are multiple paths leading to the same position. Some general rules, however, apply universally. The job of an incident responder is rarely, if ever, an entry-level position.
At a minimum, employers will want a candidate to have worked several years as part of a security team in an organization similar to theirs. Familiarity and experience with security principles as well as defensive strategies, tactics, and methods comprise the entry point.
Formal education requirements will vary widely from employer to employer. For those employers that generally value professional certifications, the same will apply to this role.
It is important to note that government entities and government contractors will often require that computer security incident responders obtain a security clearance.
1. Education While not always required, suggested education for someone seeking employment as a computer security incident responder includes obtaining one of the following college degrees: a BS in computer science, a BS in cybersecurity, or a BS in information technology. A master’s degree in one of these disciplines will further enhance career opportunities.
Cyberseek‘s data shows that 3 percent of employed experts have an associate degree, 56 percent have a bachelor’s, and 41 percent have a master’s degree.
2. Career path Common career paths include two to three years working as a computer security expert, security administrator, network administrator, or system administrator. Determined by an employer’s specific needs and the vertical in which they operate, other work experiences such as a forensic examiner or even offensive security experience may be expected.
3. Professional certifications A host of professional certifications demonstrate the skills and knowledge necessary for success as an incident responder. Each employer will likely value these certs differently. They include:
- Certified Information Systems Security Professional (CISSP)
- GIAC Certifications
- Certified Ethical Hacker
- GIAC Certified Forensics Analyst
- GIAC Certified Incident Handler
4. Experience Working as an incident responder generally requires prior experience in computer investigations or computer forensics.
Experience with computer forensic tools is desirable. Work experience that demonstrates an ability to write concise, easy-to-read, technical reports is a common requirement.
What is a computer security incident responder?
The computer security incident responder is the key role within an organization’s Computer Security Incident Response Team (CSIRT). This role is akin to that of any first responder. In the case of the CSIRT, they are the first to respond to a cybersecurity incident.
These incidents may, or may not, be actual cybersecurity breaches. Making that determination is a primary function of the team. A host of cyber detection tools monitor traffic and behavior patterns related to digital systems and assets.
When an anomaly is detected and reported by these tools it is the job of the incident responder to quickly make an initial determination regarding the potential threat, conduct an investigation to support or modify the initial determination, and work to identify and mitigate any actual threat that may exist.
The role of an incident responder is reactionary and can be very fast-paced during a security event. The urgency to identify and appropriately respond to what can sometimes be a virtual flood of automated alerts demands a person capable of working calmly in a high-pressure environment.
After the initial attack has been identified and controlled it is the job of the incident responder to provide investigative services. These services are needed to deliver the details required for security and development teams to implement security controls that will prevent a similar attack in the future.
Computer security incident responder skills and experience
The specific skills required by any given employer will be largely dependent on the operating systems used, systems architecture, and other factors unique to them.
Generally, the ability to demonstrate skills related to computer investigations and forensics will be needed. Familiarity with industry-standard forensic tools is important.
Communication skills, both verbal — in the midst of a high-pressure event — and written are critical. Written communication skills must include an ability to translate highly technical details into easily understood reports.
Management teams and even law enforcement rely on reports from incident responders to gain a clear and accurate understanding of the situation.
According to Cyberseek‘s data, here are the top skills and the projected future skills:
Top skills requested:
- Incident Response
- Cyber Security
- Incident Management
- Computer Science
- Cyber Threat Intelligence
- Security Information And Event Management (SIEM)
- Vulnerability
- Triage
- Linux
Future projected skills:
- Threat Hunting
- Security Information and Event Management (SIEM)
- Anomaly Detection
- Security Insider Threat Management
- Counter Intelligence
What do computer security incident responders do?
Often working within the security operations center (SOC), the primary responsibility of an incident responder is to rapidly investigate and document cybersecurity incidents within an organization.
Once a possible incident has been identified through either automated or manual tools, the incident responder is tasked to investigate the event and mitigate potential damages.
As a member of the CSIRT, the incident responder works closely with the enterprise’s security organization to categorize and classify attack methods and intended payloads in support of an effort to build protection for further similar incidents.
Often called a CSIRT engineer or intrusion analyst, the incident responder uses various computer forensic tools to examine and analyze a myriad of digital anomalies that could potentially lead to the discovery of an attempted breach or the existence of an advanced persistent threat within the organization’s systems. They work as part of a cybersecurity investigative team.
An incident responder will often be called upon to write reports that document their findings relative to cybersecurity investigations. These reports must reflect a technical understanding of the subject incident and yet use language that can be digested by management or other non-technical readers.
These reports can, on occasion, be used as evidence in the legal prosecution of hackers. An incident responder may be called upon to testify in court.
Computer security incident responder job description
The Computer Security Incident Responder is responsible for the identification, investigation, and resolution of security incidents detected by those protective or detective measures in place.
This role coordinates and communicates with internal stakeholders and external partners to ensure the integrity and safety of enterprise data, systems, and operations.
Key Responsibilities:
- Monitor and analyze network traffic, system logs, and other data sources to identify potential security incidents.
- Investigate alerts and suspicious activity to determine if an incident has occurred.
- Contain affected systems and networks to prevent the incident from spreading.
- Implement temporary measures to mitigate the impact of the incident.
- Work with other teams, such as IT and security operations, to develop and implement a containment strategy.
- Analyze incident data to determine the root cause of the incident and identify recommendations for improvement.
- Document and report incidents to the incident response team and other relevant stakeholders.
- Develop and implement security plans, policies, and training to prepare the organization to respond efficiently and effectively to cyber threats.
Common job titles for this role:
- Cybersecurity Incident Response Analysts
- Incident Response Analysts
- Incident Response Specialists
- Information Security Analysts
- Computer Network Specialists
Outlook for computer security incident responders
The demand for incident responders is expected to grow significantly in the foreseeable future. According to IDC, cybersecurity will be among the 20 most in-demand IT roles for the next decade. Incident response is one of the fastest-growing career segments within cybersecurity.
While some cybersecurity duties can be automated with new technology, the tasks of an incident responder are not in this class. All indications are that those individuals with the proper experience and skill set are expected to be employable for many years to come.
How much do computer security incident responders make?
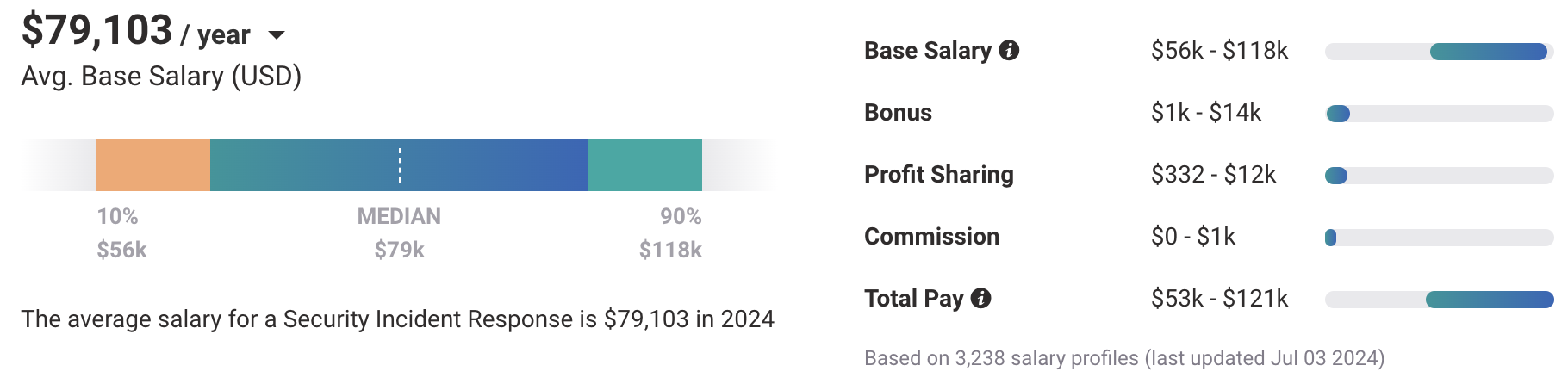
The average annual salary as of 2024 for the cyber security incident responders researched for this guide is $116,028. While ZipRecruiter is seeing annual salaries as high as $162,000 and as low as $65,500.
The average pay range for an Incident Responder according to Payscale is from $56,000 to $118,000, which suggests there may be many opportunities for advancement and increased pay based on skill level, location, and years of experience.
Frequently asked questions
Computer security incident responder investigates, analyzes, and responds to cyber incidents within the network environment.
The primary responsibility of an incident responder is to identify, and investigate security incidents (automatically or manually) and document them as soon as possible.
BS in computer science, a BS in cybersecurity, or a BS in information technology is suggested but a master’s degree in one of these disciplines will further enhance career opportunities. Professional certifications will likely valued differently. Experience with computer forensic tools is desirable but work experience that demonstrates an ability to write concise, easy-to-read, technical reports is a common requirement.
Although some cybersecurity tasks can be automated with new technologies, incident response is not one of them. As the demand for incident responders grows, the number of jobs available will also grow. All indications are that those individuals with the proper experience and skill set are expected to be employable for many years to come.
Familiarity with industry-standard forensic tools is important as well and skills related to understanding legacy such as cutting-edge attack vectors are essential.