To become a Chief Information Security Officer (CISO), you should follow key steps. Begin by earning a relevant degree in computer science or information technology. This educational foundation will provide you with a solid understanding of the field.
Ad
cybersecurityguide.org is an advertising-supported site. Clicking in this box will show you programs related to your search from schools that compensate us. This compensation does not influence our school rankings, resource guides, or other information published on this site.
Featured Cybersecurity Training
| School Name | Program | More Info |
|---|---|---|
| UC Berkeley School of Information | Online MS in Cybersecurity | No GRE/GMAT Required | website |
| Georgia Tech | Online MS in Cybersecurity | Tuition under $10k | website |
| Purdue Global | Online MS in Cybersecurity Management | website |
| Southern New Hampshire University | Online BS in Cybersecurity or Online MS in Cybersecurity | website |
| Syracuse University | Online MS in Cybersecurity | Complete in 15 Months | website |
Next, gain practical experience by working in various information security roles, such as security analyst or network administrator. Accumulating several years of experience in areas like vulnerability management, incident response, and risk assessment is crucial.
Obtain industry certifications like Certified Information Systems Security Professional (CISSP), Certified Information Security Manager (CISM), or Certified Information Systems Auditor (CISA) to showcase your knowledge and commitment to information security.
Developing strong leadership and management skills is also important, as CISOs must communicate effectively, lead teams, and make strategic decisions. Consider participating in management training programs and taking on leadership roles to enhance these abilities.
At corporations, it’s a c-suite level position, meaning one of the most powerful and influential officers in any given company, and generally reports directly to the CEO. As such, it’s a position that requires extensive experience, knowledge, expertise, and hands-on skills in as many aspects of information security as possible.
Five steps to become a chief information security officer
1. Self-analysis: The chief information security officer is not a career path suited to everyone. It requires exceptional drive, determination, dedication, leadership skills, an ability for forward-thinking, and a desire to remain continually educated on the latest trends in the field.
By the very nature of c-suite positions, chief infosec officers also interface with most other departments within the same organization, and with high-ranking officials in other companies, as well as government agencies.
Successful CISOs must possess a high level of each of these qualities, and more, to excel. So be honest in the self-assessment before deciding to charge ahead on a career targeted at becoming a chief information security officer.
2. Education: Laying the groundwork for a future in a position with such wide-reaching and varied responsibilities as a chief infosec officer can take any number of forms. A bachelor’s degree in any infosec discipline or business administration is a good starter, but nearly any computer-related or business management field could do just fine.
Security training for protecting people and facilities may also serve as a great kick-start. Of course, for C-suite officers like CISOs, additional education is often, if not usually expected. Master’s degrees and, when desired or required, doctorate degrees in more focused fields under the infosec umbrella will serve you best.
3. Career path: As with education, career paths following an almost endless variety of permutations can lead to chief infosec officer positions. The possibilities are far too numerous to list here.
For invaluable insight into how best to work toward being a CISO and how the position is evolving now and in the near future, watch this CyberSpeak interview of long-time infosec professional and current CISO Joshua Knight of Dimension Data.
Also, it is helpful to review the education and experience requirements listed by the EC-Council for a candidate to be eligible to take the exam for the certification of chief information security officers.
4. Professional certifications: Here too, there are dozens of certifications that can help a candidate attain the level of CISO. It’s probably best to remember to add certifications in every discipline worked in along the way, and any ancillary specialties that may apply to the positions on a resume.
The CCISO certificate is the pinnacle achievement for chief infosec officers. Also valuable are the training opportunities and certifications offered by such organizations as OSCP, SANS Technology Institute, ISFCE, IACIS, GIAC, CISSP, (ISC)2, IEEE, Cellebrite, AccessData, BlackBag, and EnCase.
More basic certifications, such as CompTIA A+, which certifies IT operational and technical support skills, can also be helpful. ISACA (Information Systems Audit and Control Association) offers a certification directed at infosec managers – Certified in the Governance of Enterprise IT (CGEIT), and another directed at infosec auditors, called Certified Information Systems Auditor.
5. Keep current: As is the case in most cybersecurity career positions, it is vital to remain current with what is happening in the industry. Keeping skills and knowledge up to date with the latest trends is even more critical for CISOs as they are charged with deciding how the entirety of any company’s varied infosec resources will be deployed now and in the future. Being a member of any and all relevant information security trade associations and training organizations is imperative for infosec leaders.
Two such professional trade associations are The International Society of Forensic Computer Examiners®, or ISFCE, and The Scientific Working Group on Digital Evidence (SWGDE). Another source of articles and information on specific subjects in infosec is SearchSecurity. EC-Council also provides articles, podcasts, etc. by other CISOs on its CISO Resources page.
The Information Systems Audit and Control Association (ISACA) is also a great source of training and professional interaction. Infosec Institute offers a variety of resources and training for Infosec professionals. This interview by IBMBusinessInstitute with Glen Gooding, Director of IBM Institute for Advanced Security, discusses the ever-changing infosec world and the CISOs continually evolving role within the industry.
What is a chief information security officer?
CISOs are alternatively known as chief security architects, corporate security officers, security managers, or information security managers. Some companies entrust this officer-level person with all aspects of security within the organization, including employees and facilities. In these cases, the position may carry the title of chief security officer.
A CISO by any name is still the head of all information security operations within a given organization. Chief infosec officers usually report directly to the CEO (chief executive officer) and sometimes are afforded a seat on the board of directors.
CISOs are tasked with determining the overall direction of the infosec resources under his/her domain, how the resources will be apportioned within the various disciplines, managing all of the people in his/her department, and interacting with all other departments in the organization.
CISOs are often the face of an organization’s infosec operations in interaction with outside actors. In larger corporations in particular, this may often entail dealing with government oversight, regulatory agencies, policymakers, and law enforcement agencies.
Chief information security officer skills and experience
Specific skill requirements likely to be encountered by employers include:
- Significant experience with business management and a working knowledge of information security risk management and cybersecurity technologies and strategy
- Strong understanding of Linux, virtualization, and networking concepts
- Familiarity with industry security standards including NIST, ISO, SANS, COBIT, CERT
- Familiarity with current data privacy regulations, including GDPR and regional standards.
- Strong understanding and experience with Secure SDLC and DevSecOps or security automation
- Capable of understanding and communicating the business and profit impact that infosec operations have on the organization
Because chief information security officers are at the top of the infosec heap, there aren’t a lot of certifications recognized for the position. EC-Council provides the most highly sought-after program, called Certified CISO, or CCISO.
Soft skills sought by employers include Superior interpersonal, written, and oral communication skills, the ability to work under pressure, organized and flexible, strong leadership skills experience in strategic planning and execution.
What do chief information security officers do?
Information security in the 21st century has become one of the most critical operations in any organization. The chief information security officer is responsible for providing direction, processes, and resources for every aspect of the infosec operation.
The direction and processes must be continuously reviewed, reimagined, and revamped to keep pace with changes in the infosec world at large, as well as compliance, regulatory, and legal requirements. The CISO must also be a motivational leader, as well as an interdepartmental and inter-organizational communicator of an organization’s infosec direction and processes.
There are considered to be five “towers” of responsibility within the typical CISO’s purview. Chief infosec officers must have extensive experience and knowledge in each of these towers.
- Governance and risk management (policy, legal, and compliance)
- Information security controls, compliance, and audit management
- Security program management & operations
- Information security core competencies
- Strategic planning, finance, procurement, and vendor management
The relative weight and importance of each varies from organization to organization, but these represent the focus areas for gaining experience in order to be competitive for a CISO position.
Chief Information Security officer job description
Potentially, tasks will include some or all of the following:
- Design and develop an information security program roadmap to align and scale with company growth
- Lead security assessment and testing processes, including but not limited to penetration testing, vulnerability management, and secure software development
- Develop and extend security tooling and automation efforts across the organization
- Proactively identify security issues and potential threats and continuously build processes and design systems to watch for and protect against them
- Lead compliance activities including external audits, regulatory compliance projects, and overall information security reviews
- Communicate infosec operational goals, direction, and business impact to c-suite officers and the board of directors
- Interface with outside stakeholders, partners, compliance agencies, and regulatory and legal authorities
- Provide strategic risk guidance and consultation for corporate IT projects, including the evaluation and recommendation of technical standards and controls
- Establish and implement a process for incident management to effectively identify, respond, contain, and communicate a suspected or confirmed incident
Outlook for chief information security officers
According to InfoSec Institute, there is a worldwide shortage of nearly three million in the ranks of cybersecurity professionals, half a million in North America alone.
Demand for qualified infosec employees significantly outstrips supply in nearly every specialty under the information security umbrella. As a percentage of the demand, this shortfall becomes magnified as we climb higher up on the organizational chart.
The availability of candidates capable of managing any organization’s entire infosec operation thus becomes even more glaring. It is also an even more vexing problem to overcome because it takes so long to groom candidates for these higher-level posts.
There is no shortage of interesting, prestigious, and exciting opportunities for qualified CISOs. A quick search of open positions shows such organizations as the National Security Agency (NSA), several large national and international banks, at least two state governments, and several large healthcare companies.
How much do chief information security officers make?
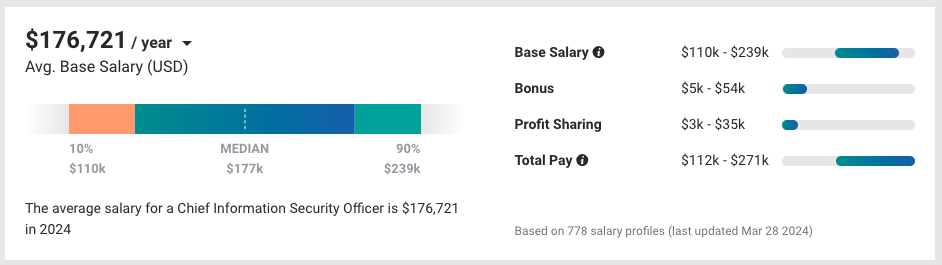
In 2024, Payscale.com reports that chief information security officers are making from about $110,000 to about $239,000 per year, with an average annual salary of $176,721.
Looking for more information about careers in cybersecurity? Learn more.
Frequently asked questions
A CISO is the person in charge of the entire information security operations of an organization. They usually report directly to the CEO (chief executive officer), and sometimes are afforded a seat on the board of directors.
Chief information security officers are responsible for ensuring the security of an organization’s information system. Among the duties they are assigned are how the resources will be allocated between the different departments as well as how they will interact with other departments within the organization.
Getting an undergraduate degree related to information security or business administration is a great place to begin with. A security training course can also serve as a great starting point. C-suite officers like CISOs, are often expected to have additional education. However, a master’s or a doctoral degree focused on information security will serve you best.
Cybersecurity professionals are in short supply worldwide, with half a million alone in North America, according to InfoSec Institute. That being said, almost every specialty under the umbrella of information security has a significant shortage of qualified employees,
Aside from soft skills sought by employers which include strong leadership skills, there are also specific skills requirements and experiences that are most likely to be encountered such as familiarity with current data privacy regulations, security standards, security automation, and more. EC-Council provides a CCISCO certification which is a most highly sought-after program since there aren’t a lot of certifications recognized for CISOs.
The amount of experience needed can vary depending on the organization and its requirements. Generally, several years of practical experience in information security roles, such as security analyst or network administrator, are necessary to become a CISO.
Yes, certifications such as Certified Information Systems Security Professional (CISSP), Certified Information Security Manager (CISM), or Certified Information Systems Auditor (CISA) can be beneficial for aspiring CISOs, as they demonstrate expertise and commitment to the field.
While prior leadership or management experience is not always mandatory, developing strong leadership and management skills is crucial for a CISO, as they need to effectively lead teams, communicate with stakeholders, and make strategic decisions.
Pursuing an advanced degree, such as a master’s in information security, can provide a deeper understanding of the subject matter and enhance your qualifications. However, it is not always a strict requirement to become a CISO.
The responsibilities of a CISO typically include developing and implementing information security strategies, managing security operations, conducting risk assessments, overseeing incident response, ensuring compliance with regulations and standards, collaborating with other departments, and providing guidance on security-related decisions.