- Career steps
- Career overview
- Important skills
- What do sec code auditors do?
- Job description
- Salary and outlook
Security code auditors are like the special forces of cybersecurity teams. Also known as an IT auditor, security auditor, secure code auditor, source code auditor, security analyst, or information security analyst, professionals lucky enough to find themselves in this role are accomplished and highly valued.
Ad
cybersecurityguide.org is an advertising-supported site. Clicking in this box will show you programs related to your search from schools that compensate us. This compensation does not influence our school rankings, resource guides, or other information published on this site.
Featured Cybersecurity Training
| School Name | Program | More Info |
|---|---|---|
| Southern New Hampshire University | Online BS in Cybersecurity or Online MS in Cybersecurity | website |
| Grand Canyon University | Online BS in Cybersecurity | website |
| Purdue Global | Online BS in Cybersecurity | website |
| Arizona State University | Online BS in Information Technology - Cybersecurity | website |
| UC Berkeley School of Information | Online Master’s in Cybersecurity | No GRE/GMAT Required | website |
Security code auditors must be versed in computer programming, systems and network security, penetration testing, cryptography, and software security protocols.
Only cybersecurity professionals with a broad-based background in the field will be effective as security code auditors. In many cases, source code audits are performed by independent outside consultants hired periodically to review an organization’s security status.
Organizations with substantial cybersecurity budgets are much more likely to hire a full-time security code auditor than those with a small information security staff.
Four steps to becoming a security code auditor
1. Education Security code auditor roles require a broad knowledge of computer science, networks, systems, and all things information security. A college education should be broad-based as well.
Degrees in computer science or a cybersecurity-related field are recommended. Coursework should include as broad a variety of cybersecurity disciplines as possible. Look to add to your college courses:
- penetration testing
- cryptography
- cybersecurity law
- computer forensics
- networking
- programming in several languages
- database security
- software engineering
Cyberseek‘s data shows that 58 percent of employed IT auditors have an associate degree, 39 percent have a bachelor’s, and 2 percent have a master’s degree.
And of course, as with any advanced cybersecurity career, investing in time and money to obtain a master’s degree can be well worth the effort.
2. Early career path As a security code auditor is not an entry-level position, the proper jobs used to break into the cybersecurity field will provide a strong foundation for a career. Good beginning infosec posts for leading to a career in security code auditor include:
- Security administrator
- Network administrator
- Digital forensics
- Vulnerability assessor
- Penetration tester
- Software developer
- Security engineer
- Penetration tester
- IT auditor
- Security analyst
- Information security analyst
3. Professional certifications Employers are always looking for verifying evidence that a prospective candidate has learned all the necessary aspects of the position being sought. In cybersecurity, probably the best way to accomplish this confirmation is through professional certifications.
Several cybersecurity organizations and continuing education venues provide a host of certifications in the most relevant infosec disciplines. Some of the certifications that should be sought by would-be or current security code auditors include the following:
- Certified Information System Auditor (CISA)
- Certified Information Systems Security Professional (CISSP)
- Certified Internal Auditor
- Institute Of Internal Auditors (IIA)
- Certified Public Accountant
Also, look for other appropriate certifications offered by such cybersecurity education organizations as the following:
- ISFCE (International Society of Forensic Computer Examiners)
- IACIS (The International Association of Computer Investigative Specialists)
- CISSP (Certified Information Systems Security Professional)
- (ISC)2 (International Information Systems Security Certification Consortium)
4. Never stop learning Computer technology and cybersecurity techniques are forever evolving, sometimes at a breakneck pace. Keeping current on all that happens in all relevant aspects of security code auditing is essential to maintaining an edge and having a long successful career.
Join professional trade associations, seek relevant continuing education opportunities, network with other code auditors, and attend seminars related to the field. Among trade associations, consider joining some or all of the following:
- The Scientific Working Group on Digital Evidence (SWGDE)
- Information Systems Audit and Control Association (ISACA)
- The International Society of Forensic Computer Examiners®
What is a security code auditor?
Code is the brain of all computer systems. If anything is wrong with the brain, the entire system becomes vulnerable to problems, errors, and especially incursion from outside sources wishing to create havoc, disrupt operations, or steal secure information.
Security code auditors are the brain surgeons of computer systems. They analyze, diagnose, and develop treatment plans for repairing any potentially problematic code vulnerabilities.
To evaluate the security of computer system code, source code auditors must be familiar with and knowledgeable of all aspects of hardware, software, and networks that comprise a complete system.
The range of skills and experience required means security code auditors are one of the most technically skilled members of any cybersecurity staff.
As the responsibility can be daunting for even the most experienced security auditors, analytical tools to assist in taking on the job have been developed.
There are numerous open-source and commercial source code analysis tools to help security code auditors uncover code vulnerabilities in hardware and software. These programs are also referred to as Static Application Security Testing (SAST) tools and can be invaluable aids.
Still, security code auditors must be able to sift through code line by line to uncover, determine the nature of, and develop a plan for the remedy of any problems.
Security code auditor skills and experience
To be able to thoroughly audit any organization’s infosec status, a variety of knowledge and skills are required. Familiarity with penetration testing techniques, current cryptography protocols, network and systems security processes, software security vulnerabilities, and more must all be in the source code auditor’s bag of tricks.
The list of required skills and experience in security code auditor job listings, therefore, is often numerous. Here is a sampling of some of the more common requirements.
- Programming languages (e.g., Java, Python, C/C++, JavaScript)
- Software development methodologies (e.g., Agile, Waterfall)
- Software development tools (e.g., IDEs, compilers, debuggers)
- Operating systems (e.g., Windows, Linux, macOS)
- Network security
- Cryptography
- Penetration testing
- Software security protocols
- Auditing
- Accounting
- Internal Auditing
- Internal Controls
- Risk Analysis
- Information Systems
- Finance
- Public Accounting
- Risk Management
Soft skills often required by employers include the following:
- Detail-oriented
- Highly analytical
- Self-motivated
- Strong written and oral communication skills
Future skills that may be requested:
- Blockchain
- Security Roles & User Privileges
- User Security Management
- Security Insider Threat Management
- ISO 27001
What do security code auditors do?
Information technology in any organization is a multi-faceted enterprise consisting of hardware systems, communications networks, software programs, and all of the protocols, permissions, procedures, and policies that determine the use of IT systems.
Security code auditors are responsible for ensuring the security of all aspects of the IT systems they oversee. Fulfilling this responsibility requires planning, executing, and analyzing the results of exhaustive audits of every nook and cranny.
This means being intimately familiar with programming codes used to write the programs running the systems, as well as all security procedures in place within the organization and the laws affecting cybersecurity methodology.
It also means being familiar with current techniques and procedures in use by hackers and having an up-to-date understanding of the most commonly exploited system vulnerabilities.
In short, security code auditors must know every minute detail of every aspect of the IT systems in use by the organization paying the professional’s salary. Source code auditors must plan and execute the most effective and thorough audits possible to persistently determine the effectiveness of all security systems in place.
It’s primarily a preemptive strategy to close vulnerabilities before they are taken advantage of by hackers. But security code auditors must also perform or assist in the performance of forensic examinations of attacks on the system, whether the attempts are failed or successful.
The answers found after such attacks must then be reported on and utilized to further tighten system security measures. In a world with constantly changing and advancing technologies and hacking techniques, the job of a security code auditor is never completely done.
Security code auditor job description
Some of the most common security code auditor tasks are as follows:
- Review source code to identify potential security vulnerabilities and risks.
- Use static code analysis tools to scan code for potential vulnerabilities without running it.
- Use dynamic analysis tools to run the code to identify vulnerabilities that may occur during runtime.
- Perform manual code review to identify vulnerabilities that may not be detected by automated tools.
- Work with developers to remediate the security vulnerabilities that have been identified.
- Document the audit findings and provide recommendations to the development team.
- Keep up-to-date with the latest security threats and vulnerabilities.
- Conduct penetration testing to simulate attacks on a system to identify vulnerabilities in code.
- Provide security training to developers on security best practices.
- Assess the risks associated with the software.
Common job titles:
- IT Auditors
- Auditors
- Audit Supervisors
- IT Security Auditors
- Information Systems Auditors
Outlook for security code auditors
Cybersecurity professionals as a whole are in high demand, and in many cases, specific job titles are struggling for viable candidates to fill the positions.
According to InfoSec Institute, there is a worldwide shortage of nearly three million in the ranks of cybersecurity professionals, half a million in North America alone.
The need for security code auditors is difficult to pin down due to the variety of titles used to describe the role, but it’s safe to say the demand is growing rapidly and should continue to do so for the foreseeable future.
How much do security code auditors make?
With the variety of titles, the propensity of many companies to hire independent consultants, and the fairly elite nature of the position, accurate salary information is somewhat elusive.
Salary.com stated that the average Security Auditor salary in the United States is at $80,039 as of 2025, but the salary range typically falls between $59,013 to $98,295.
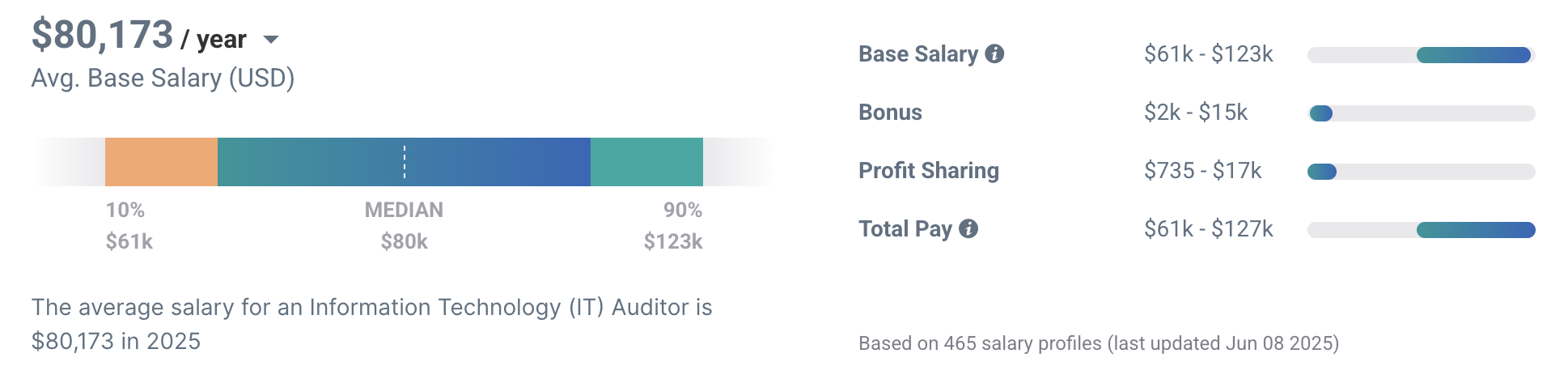
Meanwhile, Payscale‘s data shows that the pay range for IT Auditors is from $61,000 to $123,000, with an average of $80,173.
Frequently asked questions
A security code auditor is a professional who specializes in reviewing and assessing the security of computer code. Their role is to identify vulnerabilities and potential security risks in code that could be exploited by attackers.
The work of a security code auditor typically involves reviewing software code line-by-line to identify potential vulnerabilities and security risks. They use a variety of tools and techniques to identify issues so once vulnerabilities are identified, they work with developers to remediate the issues and ensure that the code is secure.
Many security code auditors have a degree in computer science or a related field, as this provides a strong foundation in programming languages, algorithms, and other technical skills needed in the field. Obtain relevant certifications and gain experience with auditing tools.
The cybersecurity profession as a whole is in high demand. And in many cases, specific job titles are in short supply of qualified candidates. The InfoSec Institute estimates an estimated shortage of nearly three million cybersecurity professionals worldwide.
Deep understanding of coding languages, security protocols, and industry standards. Must be able to recognize potential security vulnerabilities and provide solutions to mitigate the risks.
Sources
- Security Code Auditor career pathway | Sourced from cyberseek.org in Sep 2025.
- Salary info for Security Auditors | Sourced from Payscale.com and Salary.com in Sep 2025.