- Career steps
- Career overview
- Important skills
- What do security analysts do?
- Job description
- Salary and outlook
A cybersecurity analyst or information security analyst can refer to a lot of different kinds of jobs within the security profession.
Roles and responsibilities will vary based on variables such as industry and company size, but a cybersecurity analyst is generally responsible for keeping tabs on security threats to computing systems and networks.
Ad
cybersecurityguide.org is an advertising-supported site. Clicking in this box will show you programs related to your search from schools that compensate us. This compensation does not influence our school rankings, resource guides, or other information published on this site.
Featured Information Security Training
| School Name | Program | More Info |
|---|---|---|
| Southern New Hampshire University | Online BS in Computer Science - Information Security | website |
| UC Berkeley School of Information | Online MS in Cybersecurity | No GRE/GMAT Required | website |
| Arizona State University | Online BS in Information Technology - Cybersecurity | website |
Another aspect of cybersecurity analyst roles is developing proactive security strategies such as deploying specialized (and up-to-date) hardware and software. Lastly, information security analysts are also responsible for developing security-related audits, and assessments, and conducting continual monitoring of systems.
The job responsibilities of a security analyst can range from controlling file access and credentialing to maintaining firewalls and network updates, to proactively trying to hack systems to look for vulnerabilities and weaknesses.
Like other job titles within the cybersecurity industry, a security analyst is best prepared by having a bachelor’s degree in cybersecurity, an information technology degree, or a degree in a related field. Job experience and internships, along with professional, industry-recognized certifications also help job candidates land cybersecurity analyst positions.
Four steps to becoming a security analyst
- Research: The good news is that the number of opportunities and new kinds of jobs that fall under the cybersecurity analyst position umbrella continues to evolve, which means plenty of career opportunities for cybersecurity professionals to position themselves correctly.
So, the first step in launching down the path of a cybersecurity analyst path is to understand what kind of work you want to do and then map that to the kinds of education and certification you will need. Even entry-level security analyst positions might require specialized training, so it’s best to plan. - Education: According to the Bureau of Labor Statistics (BLS) most cybersecurity analysts have a bachelor’s degree in cybersecurity (or a closely related field such as mathematics, computer science, or engineering).
However, in some instances, with the proper cybersecurity certifications (see the next point) security professionals with an associate degree and/or relevant training or background (like military service, for example) can obtain entry-level cybersecurity jobs in the private sector.
Cyberseek‘s data shows that 47 percent of employed analysts have an associate degree, 47 percent have a bachelor’s, and 5 percent have a master’s degree. - Certification: One thing that separates cybersecurity from other professions is that many jobs — both entry-level and mid-career — require some level of certification that shows proficiency in some kind of specific skill. When planning for a career in cybersecurity, it is best practice to pay attention to what kinds of certifications are required for various jobs within the field.
- Network: An important part of becoming a security analyst is developing a professional network. A network that is aligned with a specific career track will help stay informed about the latest trends and opportunities within the space.
What is a security or an info sec analyst?
Security analysts can work across the spectrum of computer and information networks. From corporate databases to banking networks and from office networks to military intelligence, security analysts can be found anywhere that large amounts of information are being stored, shared, or used by a computer.
A well-trained security analyst will probably have an advanced understanding of both hardware and software and how data is stored and managed.
The top three cybersecurity threats facing information technology networks of all scales are ransomware attacks, social engineering attacks, and the theft or compromise of sensitive information from inside an organization or company. This means that cybersecurity analysts need to be prepared to deal with a wide variety of threats and look for security issues both internally and externally.
Security analyst skills and experience
The cybersecurity skills and expertise required will vary widely from job to job. Some security analyst job openings are looking for people with specific skills, like managing a proprietary network, training other employees, or conducting penetration testing on the organization’s digital properties.
For students and early career professionals, one key tactic to understand the most valuable and marketable job skills is to study a number of different job descriptions at various kinds of employers. That research should start to show trends and reveal how current skills and experience map to opportunities. Understanding the current job market will also help make decisions about what kinds of security certifications and degrees to pursue.
Despite the wide variability of cybersecurity analyst jobs, there are a number of characteristics or skills that are common to the profession:
- Programming experience. Since cybersecurity analysts are charged with defending digital infrastructure, it makes sense that cybersecurity professionals are expected to have some base level of programming experience and familiarity with foundational programming languages such as C, C++, PHP, Perl, and Java.
- Analytical. Security analysts work with data from a variety of sources and so they need to be able to take information from many inputs to make decisions.
- Detail-oriented. Much of the work of cybersecurity analysts comes down to examining small details — like lines of computer code or network commands — that could have major impacts.
- Forward-thinking. Security analysts need to anticipate the future based on current data and trends and then make security recommendations accordingly.
According to Cyberseek‘s data, here are the top skills and the projected future skills:
Top skills requested:
- Cyber Security
- Vulnerability
- Auditing
- Computer Science
- Incident Response
- Information Systems
- Risk Analysis
- Security Controls
- Risk Management
Future projected skills:
- Public Cloud Security
- Comprehensive Software Security
- Threat Hunting
- Security Information and Event Management (SIEM)
- Threat Intelligence & Response
What do security analysts do?
A security analyst often wears a lot of hats in an organization or company. They might be part police officers, part systems designers, part policymakers, and part trainers or teachers.
While security analysts could be thought of as the first responders of the digital world, as they are often called on to triage security incidents the reality is that most cybersecurity analysts spend their time developing policies and procedures and reviewing best practices and providing training for company or organization employees.
In an optimal world, a security analyst is taking proactive steps to prevent security breaches in the first place. That could mean constantly updating systems and software, or it could mean actively looking for ways to knock down firewalls or find loopholes in computer code or operating systems.
Security analyst job description
A quick search of some of the thousands of security analyst job descriptions reveals that the available positions range from entry-level kinds of jobs to more advanced security and threat mitigation professionals.
While there is a wide variety in terms of the specific skills and certifications required for particular jobs, the California Employment Development Department has published some basic information about what some of the standard job requirements are for cybersecurity analyst jobs.
- Encrypt data transmissions and build and maintain firewalls to protect confidential information.
- Develop plans and technologies to protect computer data and files against unintended destruction or modification through malware or other attack vectors.
- Develop plans and procedures for dealing with data breaches and attacks.
- Stay current on the latest attack vectors and develop solutions to protect against them.
- Monitor computer software and current user status to protect networks and organizational information.
- Develop and carry out regular risk assessments to ensure that security best practices are being met.
- Meet with staff and train other users about security threats and how network and data users can improve individual and team information security.
Common job titles for this role:
- Cybersecurity Analysts
- Information Security Analysts
- Information Systems Security Officers
- IT Security Analysts
- Information Security Officers
Outlook for cybersecurity analysts
As the digital transformation across industries and sectors grows, security analysts will continue to be in high demand. Traditional cybersecurity analysts worked in niche industries related to vulnerable sectors of the economy such as the military, finance and banking, and the oil and gas companies.
But now, consumer companies and everyday brands are hiring cybersecurity analysts to help protect their companies and operations. The need for well-trained cybersecurity analysts is so pronounced that the Bureau of Labor Statistics predicts that employment opportunities for cybersecurity professionals will grow by 29 percent through 2034.
The projected rate of job growth is much faster than other sectors of the economy and is projected to continue to grow into the next several years as more companies and organizations begin investing in cybersecurity positions.
Cybersecurity and information security analyst salary
Besides the attraction of interesting work, the growing number of career opportunities, and the wide variety of ways to prepare for these jobs, becoming a security analyst will also lead to high earning potential.
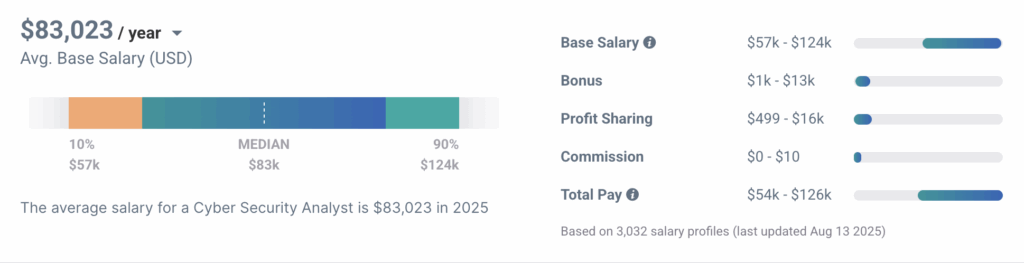
ZipRecruiter reported that the salary for a cybersecurity analyst is $99,400. The average salary range is between $43,000 and $150,000. Meanwhile, the salary range shared by Payscale.com is from $57,000 to $124,000 with an average of $83,023. Professionals with more training, experience, and educational background will earn more throughout their careers.
Looking to explore more careers in the cybersecurity field? Check out the cyber careers guide.
Frequently asked questions
A cybersecurity analyst is a professional who is responsible for protecting an organization’s computer systems and networks from cyberattacks. They are responsible for monitoring networks for security breaches, identifying potential threats, and developing strategies to protect the organization’s data and systems.
Cybersecurity analysts are responsible for protecting an organization’s computer systems and networks from cyberattacks. They must have strong technical and analytical skills, as well as excellent communication and interpersonal skills. They must also stay up-to-date on the latest cyber threats and security trends.
Learn cybersecurity fundamentals by earning a degree in a closely related field such as mathematics, computer science, or engineering. Do your research on the industry and earn a certificate
According to the Bureau of Labor Statistics, the employment rate is expected to grow by 29 percent for information security analysts throughout 2034 as the digital transformation across industries and sectors grows; security analysts will continue to be in high demand.
Cybersecurity analysts must have strong technical skills, including knowledge of programming languages, operating systems, and network protocols. They must also have strong analytical and problem-solving skills to identify and address potential security issues. Additionally, they must have excellent communication skills to effectively collaborate with other members of the organization’s security team.
Sources
- Cybersecurity Analysts career pathway | Sourced from cyberseek.org in Sep 2025.
- Salary info for Cybersecurity Analysts | Sourced from Payscale & Ziprecruiter in Sep 2025.
- Outlook info for Cybersecurity Analysts | Sourced from Bureau of Labor Statistics in Sep 2025.