- Career steps
- Career overview
- Important skills
- What do pen testers do?
- Job description
- Salary and outlook
There are many ways to become a penetration tester (often referred to as a pen tester), but they all include some form of experience with ethical hacking.
Ad
cybersecurityguide.org is an advertising-supported site. Clicking in this box will show you programs related to your search from schools that compensate us. This compensation does not influence our school rankings, resource guides, or other information published on this site.
Featured Cybersecurity Training
| School Name | Program | More Info |
|---|---|---|
| Southern New Hampshire University | Online BS in Cybersecurity | website |
| Purdue Global | Online BS in Cybersecurity | website |
| UC Berkeley School of Information | Online MS in Cybersecurity | No GRE/GMAT Required | website |
Pen testers are hired in various roles. More and more companies and organizations are hiring pen testers to test the security of networks, web applications, and other digital infrastructure where security is important.
Penetration testers are ethical hackers who perform security assessments (along with other tasks) by exercising their skills and knowledge — and get paid to perform the equivalent of digital break-ins.
They simulate cyberattacks using a broad range of tools and methods, some commercial products and some of their own creation, leaving no stone unturned to find weaknesses in networks and applications as well as people and business processes.
The idea of a penetration test, or pen test for short, is to find ways to penetrate any given computer system, to uncover gaps in security systems BEFORE the real hackers can get in. As a result, pen testers often work on highly confidential and time-sensitive projects, so being trustworthy and cool under pressure are important skills.
Having the creativity to think on the fly and being organized enough to track, record, and report on projects are also good qualities in penetration testing. It’s also important for penetration testers to have their toolset to ensure they’re up for the work at hand.
What is a penetration tester?
Penetration testers/ethical hackers are the private detectives of the information security universe. As with many private investigator (PI) operations, the task is to uncover vulnerabilities before any potential criminal hackers have a chance to implement their plans.
Some of the common job titles related to this role are the following:
- Vulnerability Management Analysts
- Vulnerability Analysts
- Vulnerability Researchers
- Vulnerability Assessment Analysts
- Security Analysts
One of the basic truths of human nature, generally, and digital information systems specifically, is that bad actors will attempt to seize opportunities to take advantage of vulnerabilities. Penetration testers seek to investigate, uncover, and aid in the repair of any potential vulnerabilities in network infrastructure devices, operating systems, and applications.
The push and pull between the pre-emptive work of penetration testers and the efforts of real-life criminal hackers is a constant arms race. Each side persistently attempts to advance its knowledge, skills, and techniques beyond the capabilities of the other side.
Penetration testers utilize a strategy of offensive defense. The goal is to provide the best possible information security by offensively attacking computer systems as a real-life hacker would, thus beating the hacker to the punch and assisting in resolving the vulnerability. The result will be added resilience and improved security controls of the information and systems under attack.
Six steps to becoming a penetration tester
Step one: Self-analysis: Penetration testing is not for everyone, but it sure is interesting for those who choose this career path.
Penetration testing requires exceptional problem-solving skills, a dogged determination to uncover weaknesses in computer systems, dedication to detail, and a desire to remain continually educated on the latest trends in the field.
Successful penetration testers must possess a high level of each of these qualities to excel. So be honest with yourself in the self-assessment before deciding whether pen testing is an appropriate career.
Step two: Education: At one time, many employers were known to hire real-world hackers and convert them from the “dark side” to work for the good guys.
In recent years, however, college degrees have become popular among penetration testers. Degrees in the various cybersecurity disciplines all provide viable entry into the field. According to Cyberseek, 44 percent earned their associate’s degree, and 54 percent graduated with a bachelor’s degree.
Formal education is not everything in this field, but it can go a long way to ensure the individual is more well-rounded and can see the bigger picture items most important to the business.
Step three: Career path: A would-be penetration tester can enter the field in several ways. Starting in security administration, network administration, network engineering, system administration, or application programming, always focusing on the security aspects of each discipline, can all provide a good foundation for penetration testing.
Step four: Professional certifications: Employers often want to see several professional certifications on the resumes of information security professionals, and this is particularly true for more senior positions.
Several organizations now offer widely recognized ethical hacking certifications for penetration testing occupations. There are also certified ethical hacker bootcamps available to help prepare for certification exams.
Step five: Honing the craft: Becoming an expert in a chosen field is a good idea in any career, but for penetration testers, there are varied ways of standing out from the crowd.
Being active and recognized in cybersecurity disciplines, such as bug bounty programs, collecting open-source intelligence (OSINT), and developing proprietary attack programs, can get penetration testers recognized among peer groups, and more importantly, potential employers or clients.
Step six: Keep current: As with most cybersecurity career paths, it is vital to remain current with what is happening in the industry.
Keeping skills and knowledge current with the latest trends in programming and network security, ever-changing hacking techniques and security protocols, popularly exploited vulnerabilities, and anything else happening in the cybersecurity industry.
Penetration tester skills and experience
Employer requirements of new hires in the penetration testing field, as in all cybersecurity disciplines, will vary dramatically depending on the detailed functions of each position and the level of the position.
Some positions still require only a demonstration of relevant skills and an appropriate level of IT and security experience and knowledge. Increasingly, though, employers are seeking candidates with a bachelor’s degree in information security or related computer science degrees. Some more advanced positions require a master’s degree in cybersecurity or a related degree, such as a master’s in information security.
Work experience that often leads to careers in penetration testing includes software development and coding, security testing, or working as a network or security engineer or administrator, security administrator.
Skill requirements likely to be encountered by employers include:
Knowledge of specific computer languages, such as:
- Python
- Powershell
- Golang
- Bash
Experience with network protocols, Windows/ Linux/ macOS, firewalls, IPS/IDS systems, virtual machine environments, data encryption, as well as iOS and Android mobile operating systems.
Knowledge of common penetration testing and application security tools, such as:
- Aircrack-ng
- Kaduu
- Kali
- Metasploit
- Burp Suite
- Wireshark
- Network Mapper (nmap)
- Nessus
- Probely
- Qualys
Top skills most commonly requested for pen-tester jobs:
- Vulnerability
- Penetration Testing
- Vulnerability Management
- Vulnerability Assessments
Technical Concepts/Areas:
- Operating Systems
- Automation
Common professional certifications often sought by employers include those available from:
- Global Information Assurance Certification (GIAC)
- Offensive Security Certified Professional (OSCP)
- Certified Information Systems Security Professional (CISSP)
- Certified Ethical Hacker (CEH)
- GIAC Penetration Tester
Check out the cybersecurity certification section for more details.
Soft skills and experience sought by employers include excellent communication skills, self-driven, creative, and resourceful; contributions to open source projects and bug bounty programs; and familiarity with OWASP Top 10 vulnerabilities.
What do penetration testers do?
Generally speaking, penetration testers typically perform threat modeling, vulnerability scanning, and ethical hacking of networks, operating systems, and web-based applications. More specifically, assurance validation involves some or all of the following tasks:
- Gather and analyze Open Source Intelligence (OSINT) to find information disclosures.
- Provide subject matter expertise focusing on offensive security testing operations, working to test defensive mechanisms in an organization.
- Assist in the scoping of prospective engagements, leading engagements from initial stages through implementation and remediation.
- Conduct assessments on a wide variety of technologies and implementations, utilizing both automated tools and manual techniques.
- Develop scripts, tools, and methodologies to enhance testing processes.
- Conduct social engineering exercises and physical penetration tests.
- Test both wired and wireless networks for security vulnerabilities.
- Examine assessment results to identify findings and develop a holistic analytic view of the system within the environment in which it operates.
- Identify the root cause of technical and non-technical findings.
- Publish an assessment report that documents findings and identifies potential countermeasures.
- Track findings that are repeated across multiple assessments and communicate these findings.
- Upon completion of assessments, communicate methods employed, findings, and analytics.
- Provide technical support to information security managers in remediating assessment findings.
- Provide technical support in network exploitation and evasion techniques to assist in comprehensive incident handling and forensic analysis of compromised systems.
Sample penetration tester job description
Penetration testing/ethical hacking job scopes vary widely based on the employer and seniority level. Looking at stated responsibilities for senior-level positions provides insight into the eventual dream job for all ethical hackers. This real-life job description gives you an idea.
- Lead enterprise and system-focused network and application penetration assessments to identify security risks and vulnerabilities.
- Perform testing on a wide scope of systems, including web applications, security controls, network infrastructure, wireless, and mobile deployments.
- Conduct hands-on technical testing beyond the use of automated tool validation. Plan, execute, report, and lead technical debriefs on testing activities and outcomes.
- Execute covert Red Team operations to mimic adversary tactics and work closely with a Purple Team to test exploits needed to build detections.
- Communicate findings and remediation strategies effectively to stakeholders, including technical staff and executive leadership.
- OSCP, GPEN, or GXPN certification preferred.
Information security needs to become front and center for all business types, and especially for those organizations dealing with state secrets, such as military suppliers and national security organizations.
Outlook for penetration testers
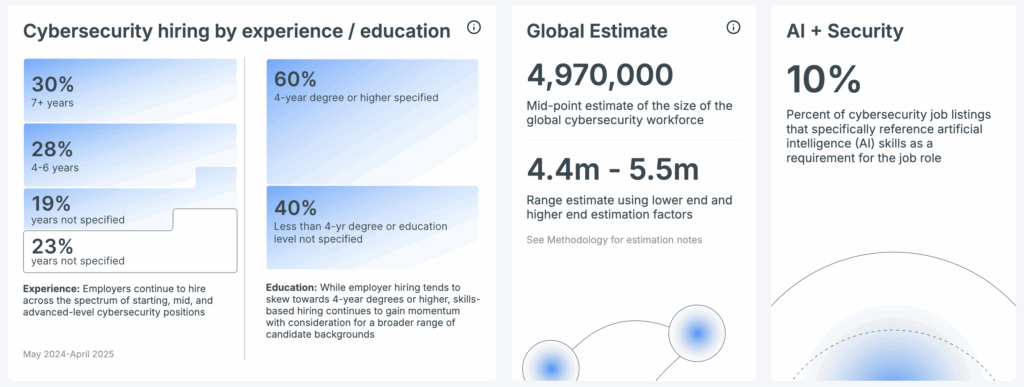
Cyberseek.org reported that from May 2024 to April 2025, 60 percent of cybersecurity job listings required a four-year degree or higher, while 40 percent did not.
This aligns with a broader tech trend—nearly half of June’s job ads, including positions in network support and web development, didn’t list a college degree as a requirement.
During that same 12-month period, Cyberseek also recorded 4,666 online job listings for Penetration & Vulnerability Tester roles.
Information security professionals focusing on penetration testing will be in high and rapidly growing demand for the foreseeable future. There is a significant shortage of information security professionals across all disciplines, and the shortage is expected to persist for the foreseeable future.
As networks, applications, and information management needs become consistently more complicated and critical to business and state operations, these systems become more directly targeted and more vulnerable.
Penetration testers are at the forefront of technical expertise, acting most closely to the role of would-be attackers.
How much do penetration testers make?
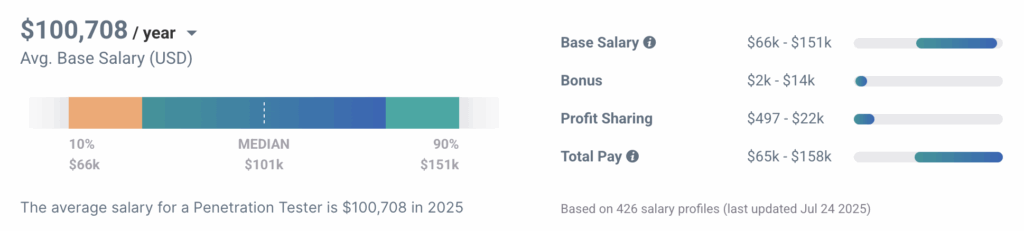
Payscale reports that penetration testers make from about $66,000 to about $151,000 per year, with an average annual salary of $100,708.
Looking for more information about careers in cybersecurity? Check out all of the related career profiles.
Frequently asked questions
A penetration tester, also known as a pen tester or ethical hacker, is an individual who is hired to attempt to gain unauthorized access to a computer system, network, or application. The purpose of a penetration test is to identify security vulnerabilities that an attacker could exploit and to determine the effectiveness of the existing security measures.
Penetration testers use a variety of tools and techniques to identify and exploit security vulnerabilities. These tools and techniques include port scanning, vulnerability scanning, password cracking, social engineering, and exploitation of known vulnerabilities. Penetration testers also use manual techniques such as reverse engineering and code review to identify security flaws.
The outlook for penetration testers is very positive. As organizations become increasingly aware of the need to protect their networks and data from malicious actors, the demand for penetration testers is expected to grow.
As a penetration tester, you’d need to have a combination of technical knowledge, problem-solving skills, and an understanding of the security landscape. Develop your technical skills, expand your network, and get certified so you can build your portfolio.
Sources
- Penetration tester career pathway | Sourced from cyberseek.org in Sep 2025
- EC-Council Training and Certifications | From EC-Council in Sep 2025
- (ISC)2 Cybersecurity Certifications and Continuing Education | From (ISC)2 in Sep 2025
- OSCP Certifications | From OffSec in Sep 2025
- GIAC Certifications | From GIAC in Sep 2025
- Salary information for Penetration tester | Sourced from Payscale.com in Sep 2025