- Career steps
- Career overview
- Important skills
- What do infosec manager do?
- Job description
- Salary and outlook
If you want a constantly in-demand career in technology, consider becoming an information security manager. The need for cybersecurity experts is expected to significantly increase in the next decade.
Ad
cybersecurityguide.org is an advertising-supported site. Clicking in this box will show you programs related to your search from schools that compensate us. This compensation does not influence our school rankings, resource guides, or other information published on this site.
Featured Cybersecurity Training
| School Name | Program | More Info |
|---|---|---|
| Purdue Global | Online BS in Cybersecurity | website |
| UC Berkeley School of Information | Online Master’s in Cybersecurity | No GRE/GMAT Required | website |
| Arizona State University | Online BS in Information Technology - Cybersecurity | website |
| Southern New Hampshire University | Online BS in Cybersecurity or Online MS in Cybersecurity | website |
Information security managers guard an organization’s computer networks and systems against unauthorized access or use. They might install firewalls, create response plans for incidents, and make policies to keep data safe and available. They may also oversee staff who work on daily security tasks.
Ready to learn more? Here’s everything you should know about becoming an information security manager.
What does an information security manager do?
- An information security manager develops and implements policies and procedures to protect an organization’s computer networks and systems.
- They also examine reports produced by the monitoring system to look for any signs of future cybersecurity risks.
- Security managers oversee backup and security systems, recover data in case of a disaster, and conduct security violation investigations.
- Security managers also sometimes run simulated attacks to evaluate the effectiveness of security measures. Professionals in this position also ensure all data is appropriately secure, working with other IT staff members to achieve this.
- Additionally, information security managers need to educate staff about threats and the use of strong passwords and protect data while working outside the office.
- They also work with upper management to develop strategies for potential security threats. Managers and employees are assigned different levels of access to corporate data depending on their experience and role in the company.
- Information security managers must have a strong understanding of computer networks and systems. They must be able to identify potential security risks and develop strategies for mitigating those risks.
- Information security managers also need to have excellent communication skills. They must be able to explain complex technical concepts to non-technical staff members and upper management.
- Information security managers play a crucial role in avoiding disasters by identifying weak areas that might make information systems vulnerable.
- Most information security management professionals work full-time in an office environment. Some managers also manage those who telecommute and run an in-house staff.
How to become an information security manager?
There is no one-size-fits-all answer to this question, as the steps vary depending on your previous education and work experience. Yet, there are some common steps that many people take when looking to become an information security manager.
Per Cyberseek’s data, 52 percent of cybersecurity managers obtained an associate degree, 45 percent of them have earned a bachelor’s and 2 percent have pursued a master’s degree.
In most cases, people may pursue a bachelor’s degree in information security or a related field, such as computer science. Some also have a master’s degree in a related area, such as information security.
Cybersecurity-related courses usually include IT fundamentals, data and web security, technical communication, cyber law, risk management, web development, digital forensics, and related subjects.
Some Information Security Managers pursue certifications, such as the Certified Information Systems Security Professional (CISSP), Certified Information Security Manager (CISM), Certified Information Systems Auditor (CISA), GIAC Certifications, and Certified In Risk And Information Systems Control. These IT certifications may help you stand out from other candidates when applying for jobs.
Information security manager skills and experiences
Begin your information security career in entry-level roles like system administrator or security analyst, then progress to a security manager with experience. While degrees and certifications enhance employability, practical experience, often gained through initial positions or internships, is crucial for career success in this field.
Also, here are the top skills requested for cybersecurity managers:
- Cyber Security
- Computer Science
- Auditing
- Risk Management
- Project Management
- Vulnerability
- Risk Analysis
- Incident Response
- Information Systems
Projected future skills for cybersecurity managers:
- Cloud Security
- Cloud Access Security Broker (CASB) Management
- Enterprise Mission Assurance Support Service
- Cybersecurity Strategy
- Security Insider Threat Management
What are some common career paths for information security managers?
Information security managers are needed in various organizations like corporations, government agencies, and non-profits, across both private and public sectors, each presenting unique security challenges.
Your role, whether managing a team or working independently, will focus on defending data and ensuring system security, tailored to the specific threats faced by the organization’s type and size.
What are some entry-level positions in this field?
There are many entry-level positions in the information security field. These positions may include cybersecurity technician, junior security analyst, security engineer, and network administrator. These positions let you get experience and learn about technologies used to safeguard data. Typically, beginners in cybersecurity may handle backups, monitor logs, and update software.
You can find various entry-level jobs in information security tailored to your interests, such as junior digital forensic analyst or junior web security analyst. These positions provide a great start in the field, helping you gain experience and prepare for future management roles.
What are some more advanced careers?
There are many advanced careers in the field of information security. These careers may include senior security analyst, lead security engineer, and information security director, and these positions require a great deal of experience and knowledge in the field.
Senior-level cybersecurity professionals may perform threat modeling, incident response, and vulnerability management. These more advanced careers often require several years of experience working in the field.
Once you gain experience in the cybersecurity field, you may choose to move into more advanced positions, such as an information security manager or security director.
Some common job titles related to this role:
- Cybersecurity Managers
- Information Security Managers
- Directors of Cyber Security
- Cybersecurity Program Managers
- Technology Risk Managers
These jobs need you to understand technologies that protect data and to create and apply policies. You’ll work with advanced security systems and have important responsibilities to keep an organization’s data safe. You might also lead a team of security experts.
Sample job descriptions of information security manager
Description one
- In a progressive company, an experienced and motivated information security manager will be responsible for:
- Developing and implementing security policies and procedures
- Monitoring compliance with security policies and procedures
- Conducting risk assessments
- Identifying security vulnerabilities
- Developing plans to mitigate risks
- Investigating incidents
- Preparing reports for senior management
- The ideal manager candidate should have experience working in an information security role and a strong understanding of security technologies. They will also work independently and make decisions in a fast-paced environment.
Description two
- Experienced information security manager will be responsible for:
- Developing and implementing information security policies, procedures, and controls
- Conducting risk assessments and audits
- Managing incident response
- Researching and staying up to date on security trends
- Training employees on security awareness
- Requirements for this position include:
- Proven experience as an information security manager or similar role
- Experience with security frameworks
- Solid understanding of security technologies and controls (firewalls, encryption, access control, etc.)
- Excellent communication and interpersonal skills
- Strong project management and organizational abilities
Description three
- The information security manager creates and applies security rules, checks for risks, handles incident responses and research, stays current on security trends, and trains employees on security awareness.
- Requirements for this position include:
- Bachelor’s degree in Computer Science, Information Systems, or related field
- Minimum of five years experience in information security
- Experience with incident response, risk assessment, and management
- Strong understanding of security trends and technologies
- Excellent communication and training skills
What is the salary for an information security manager?
The salary for an information security manager may vary depending on the organization’s size and location.
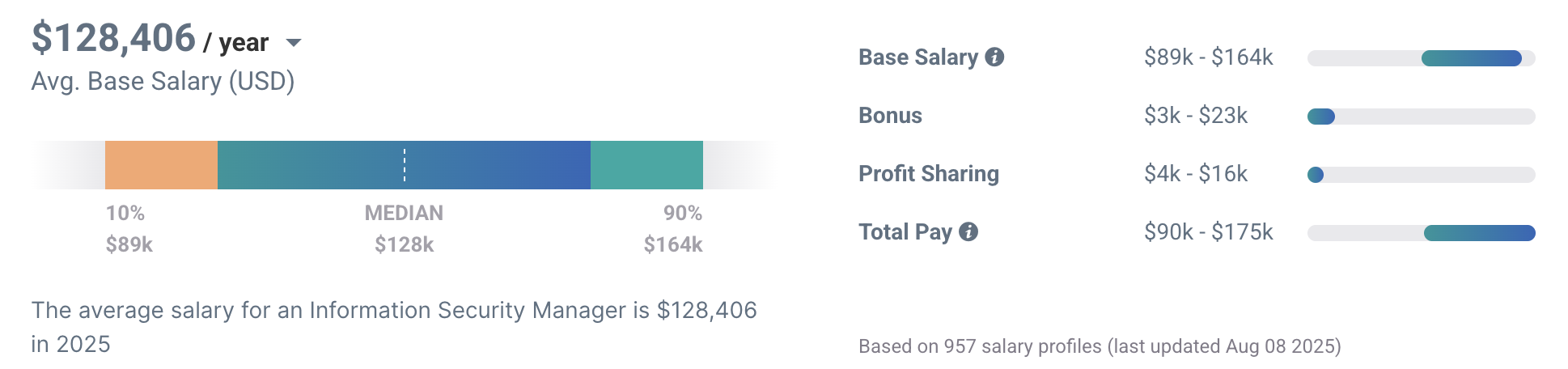
Salary.com stated that the average information security managers earn $146,745 annually, ranging from $122,924 and $167,865. Payscale showed a $89,000 to $164,000 range and an annual average of $128,406 as of 2025.
Outlook for information security manager
The outlook from the Department of Labor Statistics shows that demand for information security analysts and cybersecurity occupations will expand by 29 percent between now and 2034.
The job outlook for information security managers is positive. The demand for qualified professionals is likely to continue growing in the coming years. As security threats increase and become more sophisticated, organizations must invest in security managers to protect their data.
Bottom line
The role of an information security manager is vital to any organization in today’s climate. With the ever-growing threat of cyber attacks, it’s essential to have someone in this role who is up-to-date on the latest security trends and technologies.
To become an information security manager, you can explore numerous opportunities due to the growing demand in the field. Success in this role requires experience, a solid grasp of security technologies, and the ability to work independently and make decisions, sometimes in a fast-paced setting.
Frequently asked questions
An information security manager is a person who oversees the safety of an organization’s data. They create, put into action, and uphold rules and methods to keep the organization’s information confidential, accurate, and accessible.
Create and put into place rules to safeguard an organization’s computer networks and systems. They check reports for future cybersecurity threats, manage backup and security systems, retrieve data after disasters, and investigate security breaches.
In addition to earning a degree or certification in information security, getting hands-on experience in the field will better prepare you for a successful career.
The growing risk of cyber-attacks means information security managers must stay updated with new trends and technologies. The Department of Labor Statistics predicts that jobs for information security analysts and cybersecurity roles will grow by 29 percent from now until 2034.
Key skills in this field include technical knowledge of security principles and compliance, an understanding of best practices, and a commitment to continuous learning. Since the field always changes, information security officers must be ready to learn and adapt to new technologies and threats.
Sources
- InfoSec Manager career pathway | Sourced from Cyberseek.org in Sep 2025.
- Salary info for InfoSec Manager | Sourced from Salary.com and Payscale in Sep 2025.
- Outlook info for InfoSec Manager | Sourced from Bureau of Labor Statistics in Sep 2025.