- Career steps
- Career overview
- Important skills
- What do computer forensics do?
- Job description
- Salary and outlook
Getting a computer forensics degree opens doors for the in-demand field of computer forensics investigation.
Ad
cybersecurityguide.org is an advertising-supported site. Clicking in this box will show you programs related to your search from schools that compensate us. This compensation does not influence our school rankings, resource guides, or other information published on this site.
Featured Cybersecurity Training
| School Name | Program | More Info |
|---|---|---|
| Purdue Global | Online BS in Cybersecurity | website |
| UC Berkeley School of Information | Online Master’s in Cybersecurity | No GRE/GMAT Required | website |
| Arizona State University | Online BS in Information Technology - Cybersecurity | website |
| Southern New Hampshire University | Online BS in Cybersecurity or Online MS in Cybersecurity | website |
The rapid growth in digital and computer crime ensures interesting work and well-paying career opportunities.
Consider the following:
- The 2022 FBI Internet Crime Report showed that 800,944 cybersecurity-related crimes were reported in the United States alone. The total dollar loss to internet crime in 2022 was $10.3 billion. People aged 60 and older reported the highest losses to digital crime.
- In 2023, 5.18 billion people have access to the internet globally. That represents 64.6 percent of the planet’s population. The number of internet users and overall data creation, transfer, and storage will only continue to grow, meaning more opportunities for cybercrime and the need for computer forensics investigators.
Computer forensic investigators work within local, state, national, and international law enforcement agencies, as well as within personal investigation firms in the fight against digital and computer crimes.
The duties of a computer forensics investigator will vary depending on which of these types of organizations they are employed by.
Those looking to obtain a career in the field of computer forensics should consider pursuing a bachelor’s degree in computer forensics, computer science, cybersecurity, criminal justice, or other related fields.
Computer forensics certifications, such as those provided by the Global Information Assurance Certification (GIAC), will improve a candidate’s chance of landing a job in the field. Even obtaining more general cybersecurity certifications that are not specific to computer forensics may also improve the chances of employment.
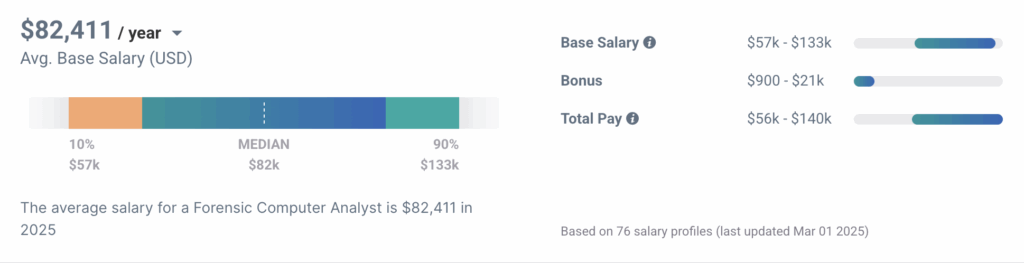
5 steps to follow when pursuing a career in computer forensics
1. Plan: Becoming a computer forensics investigator isn’t something that happens overnight. It’s best to plan out the path that you will take to reach your unique career goals.
For example, if you are hoping to pursue a computer forensics career within the government, you’ll want to understand the exact requirements for that specific position. Private, non-government-operated investigation firms are generally less stringent when it comes to their candidates’ qualifications. The first step is to determine whether you are looking to land a job within the private or government sectors.
2. Educate: The typical entry-level position within computer forensics requires a bachelor’s degree in computer forensics, computer science, criminal justice, or a related field. In some instances, it may be possible to land an entry-level role as a computer forensics investigator with an associate degree and the proper certifications.
Cyberseek reports that 52 percent of forensics investigators hold an associate degree, and 46 percent hold a bachelor’s degree.
3. Certify: Some positions within the field of computer forensics will require specific certifications such as Certified Information Systems Security Professional, Security+, and Certified Ethical Hacker.
However, even when certification is not required, having one (or many) can set you apart from other candidates. The Certified Forensic Computer Examiner and Certified Internal Auditor are widely acknowledged by both private companies and government agencies.
Another organization that offers trusted computer forensics certifications is the Global Information Assurance Certification (GIAC). There are several GIAC certifications relating to computer forensics such as GIAC Certified Forensic Analyst (GCFA), GIAC Certified Forensic Examiner (GCFE), and GIAC Network Forensic Analyst (GNFA). GIAC is also trusted by both private organizations and government entities such as the National Security Agency.
4. Apply: After obtaining the necessary degrees and certifications, it’s time to begin applying for positions. Government agencies such as the Federal Bureau of Investigation, the National Security Agency, and the Central Intelligence Agency will generally list their openings right on the careers page of their websites. Smaller, local government agencies typically have listings on their websites as well. Jobs within the private sector can be found on standard job listing sites such as Indeed, LinkedIn, and Glassdoor.
5. Keep Learning: Having a career in a field that is always changing means that the process doesn’t stop after you’ve accepted a job. It’s vital to continually improve your skills and keep learning. Attending conferences, such as RSA and BlackHat, is one great way to stay up-to-date on emerging technologies. Don’t forget to subscribe to computer forensics and cybersecurity publications to receive updates on the latest technological advancements.
What is a computer forensics investigator?
The average law enforcement agent may not be well-versed in technology. This is where a computer forensics investigator comes in. The computer forensics investigator lends their in-depth knowledge of computer systems and networks to an investigation.
Computer forensics investigators will need to understand how to retrieve data from systems that have been corrupted or damaged, with or without having the password to access the data.
The data on these systems or the systems themselves may have been corrupted unknowingly or intentionally to hide something. Computer forensic investigators should have in-depth knowledge of encryption methods and how to crack them.
The main goal of the computer forensics investigator is to find and prepare digital evidence that can be used in any court proceedings, trials, and criminal investigations.
Computer forensics investigator skills
The skills needed as a computer forensics investigator will vary greatly depending on the job.
As a baseline, anyone pursuing a career in computer forensics should focus on having an understanding of the following:
- Networking: As with any job in cybersecurity, it’s imperative to have a grasp of computer networking and connectivity concepts.
- Operating system knowledge: Computer forensic investigators will need to know how to effectively find and retrieve data from various operating systems including, but not limited to, Windows, Linux, MacOS, Unix, and Android.
- Malware analysis: At times, computer forensic investigators may be asked to analyze or reverse engineer a piece of malware. Reverse engineering and malware analysis are skills that, while they are difficult to learn, are invaluable to anyone working within computer forensics.
- Analytical skills: Because a large portion of a computer forensics investigator’s job is to analyze digital data and evidence, analytical skills are crucial.
- Cryptography: Often, the data that needs to be analyzed is encrypted. Computer forensics investigators should know encryption and decryption methods.
Top skills requested according to Cyberseek:
- Cyber Threat Intelligence
- Cyber Security
- Incident Response
- Vulnerability
- Computer Science
- Intelligence Analysis
- MITRE ATT&CK Framework
- Security Information And Event Management (SIEM)
- Digital Forensics
Projected future skills for:
- Threat hunting
- Security information and event management (SIEM)
- Anomaly detection
- Network firewalls
- Counter intelligence
What do computer forensics investigators do?
Computer forensics investigators will often do whatever technical work is needed to assist in an investigation.
Imagine a situation in which a suspect of a crime was apprehended by law enforcement for committing crimes online. The suspect has tried to wipe his or her hard drive to remove any trace of criminal activity.
The role of the computer forensics investigator in this scenario would be to attempt to retrieve the pertinent data that the suspect may have removed. This process can be done using specialized tools, as well as using forensic techniques.
Computer forensic investigators may also assist in tracking down criminals by analyzing the metadata within their online posts. Ethical hacking techniques can assist in this type of scenario.
The specific job of a computer forensic investigator will vary depending on the needs of the investigation they are working on. The above scenarios are just two potential roles a computer forensics investigator may play within an investigation.
Computer forensics investigator job description
Job descriptions within the field of computer forensics will vary greatly depending on the hiring company and whether the job is within the government role or private sector.
Job titles/openings related to this role:
- Cyber Threat Analysts
- Cyber Threat Intelligence Analysts
- Threat Intelligence Analysts
- Digital Forensics Analysts
- Crime Intelligence Analysts
While the specifics of the jobs may vary, here are a few items that are often listed in a computer forensics investigator job description.
- Work with law enforcement to recover digital evidence both onsite and in the lab
- Review digital evidence and provide findings to the appropriate members of the team
- Prepare computer and digital evidence for court proceedings
- Conducting interviews with suspects and witnesses regarding computer evidence
- Train law enforcement on what to look for when handling computer/digital evidence
- Advise law enforcement on the reliability of digital evidence
- Work with law enforcement to locate suspects using online data
- Decrypt and analyze digital data
Outlook for computer forensic investigators
Computer forensics is a newer field. With the use of technology constantly rising and criminals becoming even more active online, careers within computer forensics are likely to stick around and grow for the foreseeable future.
Both privately owned businesses and government entities such as the FBI, CIA, and NSA all need well-trained computer forensics investigators and analysts. According to the Bureau of Labor Statistics, the field of computer forensics is expected to grow by about 9 percent by the year 2034.
With artificial intelligence (AI) taking over many of the jobs that humans once held, it’s understandable for some to be concerned while thinking about pursuing a new career. If this is a concern, there is no need to fear. According to WillRobotsTakeMyJob.com, it is extremely unlikely that careers in computer forensics will become automated anytime soon.
Computer forensics investigator salary
A career as a computer forensic investigator is sure to bring excitement to your life, but with its high earning potential, it’s also sure to bring some excitement to your bank account as well.
The average salary of a computer forensics investigator, according to Payscale, is $82,411 (ranging from $57k to $133k). While Ziprecruiter‘s information is at $77,448 as of 2025, but it’s important to keep in mind that salaries vary based on location and skill set.
Those with advanced education and certifications can make upwards of $133,000 per year. An entry-level role as a computer forensics analyst will start with a salary of around $33,000 annually.
Looking for more information about careers in cybersecurity? Learn more.
Frequently asked questions
A computer forensics investigator is an expert who is trained to gather, analyze, and preserve digital evidence from computers, smartphones, and other digital devices to be used in legal proceedings. Their job is to retrieve and analyze data from devices, networks, and storage media to investigate computer-related crimes, security breaches, and other digital incidents.
Their work can involve examining digital devices for evidence of fraud, theft, intellectual property theft, and cyber attacks, among other types of crimes. They may also be called upon to testify in court as expert witnesses, providing analysis and interpretation of technical data in layman’s terms for the judge and jury.
Consider obtaining a bachelor’s or master’s degree in a relevant subject to gain a solid foundation in computer technology and forensic analysis. Seek out training opportunities and certifications to develop your skills even more.
According to the Bureau of Labor Statistics, the field of computer forensics is expected to grow by about 9 percent by the year 2034. This growth is due to the increasing importance of cybersecurity and the need to protect sensitive data from cyber threats. As more businesses and organizations rely on digital technology to store and transmit sensitive information, the demand for computer forensics investigators is likely to continue to grow.
Having a basic understanding of networking, malware analysis, analytical skills, cryptography, and operating system knowledge will be a good start for your career.
Sources
- Computer Forensics career pathway | Sourced from cyberseek.org in Sep 2025.
- Computer Forensics Salary info | Sourced from Ziprecruiter and Payscale in Sep 2025.
- Outlook info for Computer Forensics | Sourced from BLS in Sep 2025.